Kaspersky Lab analysts told about the discovery of a spy campaign that used the complex modular structure of MosaicRegressor, which, among other things, included second ever bootkit for the Unified Extensible Firmware Interface (UEFI).
UEFI attacks are the real Holy Grail for hackers. After all, UEFI is loaded before the operating system and controls all processes at an “early start”.Hence the main danger associated with compromising this environment: making changes to the UEFI code means taking complete control of the computer. For example, it allows changing memory, disk contents, or, as in the case of the MosaicRegressor bootkit, forcing the operating system to launch a malicious file.
“Since we are talking about low-level malware, getting rid of it by replacing the hard drive or reinstalling the OS will not work”, – say the experts.
However, such attacks are extremely rare. The fact is that intervention at such a low level is difficult to carry out, and attackers, in fact, need either physical access to the device, or they will have to compromise targets using complex attacks on supply chains (within which UEFI or tools working with UEFI would be modified).
As a reminder, DoppelPaymer operators published in the public domain Boeing, Lockheed Martin, SpaceX and Tesla documents, which they received during attacks on supply chains.
The first bootkit for UEFI was discovered by ESET specialists in 2018. The researchers then concluded that it was the work of the Russian-speaking government hack group Fancy Bear. Now, Kaspersky Lab researchers attribute the authorship of MosaicRegressor to Chinese-speaking hackers.
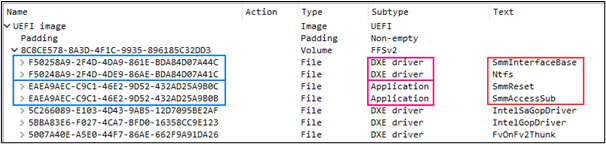
MosaicRegressor activity was detected using Firmware Scanner technology, which has been included in Kaspersky Lab products since the beginning of 2019 and was developed specifically to detect threats hidden in ROM BIOS chips, including UEFI firmware images.
In the course of researching the MosaicRegressor infrastructure, the specialists found that the components of the bootkit are based on the Vector-EDK code. This is a special constructor created by the Hacking Team, which, among other things, contains instructions for creating a module for flashing UEFI.
The Hacking Team was “leaked” into free access, which allowed attackers to create their own software with minimal effort: they simply supplemented the source code with a malicious component.
While the experts have yet to learn all the MosaicRegressor components, the one they have already covered was intended to collect all documents from the Recent Documents folder and put them in a password-protected archive. Most likely, this is how cybercriminals prepare files for theft.
“There are different methods of UEFI infection: if this microchip was not properly protected, then using a special program or even legal utilities to update UEFI, hacker can run a malicious version of the firmware. There is also a method involving physical access to equipment, – adds Igor Kuznetsov. – We are dealing with a powerful, advanced tool for cyberattacks, not every attacker can do it. However, with the appearance of ready-made working examples, there is a danger of reusing the technology, especially since anyone can still download the instructions for it. This incident demonstrates that attackers are becoming more creative and constantly improving their techniques.”
The UEFI bootkit was found on only two systems, while other MosaicRegressor components were found on many computers.
Apparently, the hackers chose the targets for their attacks very carefully, as it were only diplomats or scientific production associations in Africa, Asia and Europe.
As a reminder, during the analysis of one of hackers’ attacks, experts discovered traces of multiply Chinese government cyberoperations.