French companies are under attack via Chocolatey package manager
Hackers are abusing the popular Chocolatey package manager for Windows as part of a phishing campaign aimed at planting the Serpent backdoor on the systems of French government agencies and major construction firms.
A new phishing campaign aimed primarily at French construction and real estate organizations, as well as government agencies, was discovered by Proofpoint experts. They write that the hackers use a complex infection chain consisting of Microsoft Word documents with macros, the Chocolatey package manager, and steganography.The attack starts with a simple phishing email allegedly related to the GDPR. The email contains an attached Word document containing a malicious macro. When this document is opened, a malicious macro extracts an image of a fox from the animated series Dora the Traveler.

The image above is not as innocuous as it might first appear, as it uses shorthand to hide a PowerShell script. This script will download and install the Windows Chocolatey package manager, which will then be used to install Python and the PIP package installer.
Chocolatey is also used to avoid detection by security software, as it is often used in corporate environments and is often on the allowed list.
As a result, a second steganographic image is loaded into the victim’s system to download the Serpent backdoor, which is a malware written in Python (therefore, previously installed packages were required in the previous steps).
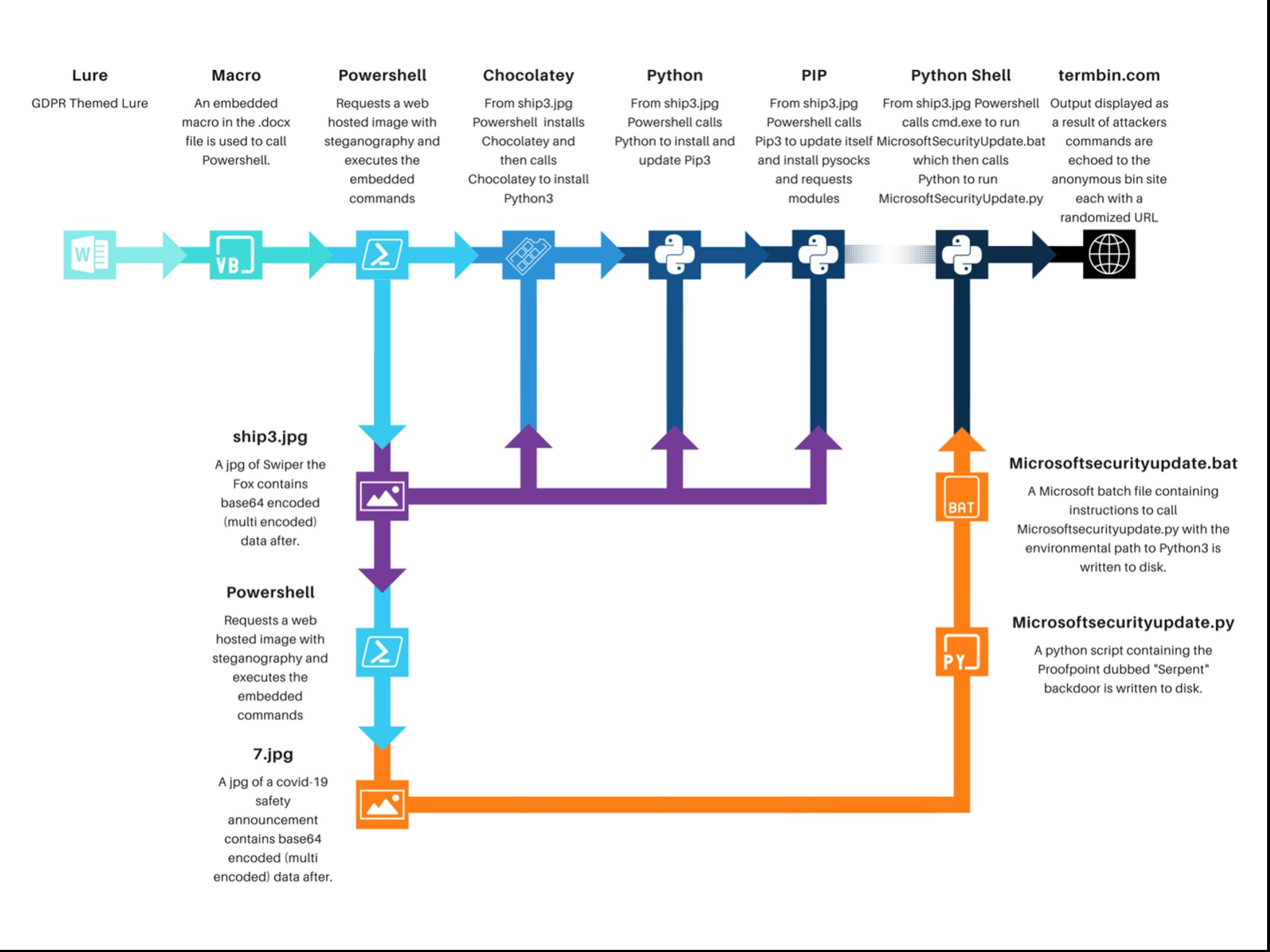
Attack scheme
Serpent, in turn, will contact the hackers’ control server to receive commands to be executed on the infected device. According to analysts, the backdoor is capable of executing any command of its operators, allowing it to download additional malware, open reverse shells, and gain full access to the device.
Let me remind you that we also talked about the fact that Hacked Oxford server was used for phishing attacks on Office 365, and also that APWG Notes Three-Year Phishing Record.





