Chinese Group Billbug Hackers Target a Certificate Authority in Asia
Since March 2022, the Chinese cyber-espionage group Billbug (aka Thrip, Lotus Blossom, Spring Dragon) has targeted a certificate authority, government agencies, and defence organizations in several Asian countries at once, according to Symantec.
The Billbug hack group is believed to have existed since 2009 and it mainly attacks organizations in Southeast Asia and the United States, and specializes in espionage and data theft.Let me remind you that we also wrote that Chinese Hack Group Aoqin Dragon Has Been Quietly Attacking Companies Since 2013, and also that Three Chinese APT Groups Attack Major Asian Telecommunications Companies.
Symantec says the Billbug group, which they’ve been monitoring since 2018, is now targeting an unnamed CA (it’s speculated to be in Taiwan – Chinese cyberspies are especially fond of the island), which would allow hackers to deploy signed malware, making it harder detection and decryption of HTTPS traffic.
At the same time, the company has no evidence that the attackers still managed to compromise digital certificates. According to the results of observations, the relevant authorities have already been notified about the events.
Analysts write that they were unable to determine how Billbug gains initial access to target networks, but it is assumed that this occurs through the exploitation of known vulnerabilities in various applications accessible via the Internet.
As in previous campaigns, hackers use tools already present on the target system, public utilities, as well as custom malware:
- AdFind;
- Winmail;
- WinRAR;
- Ping;
- Tracert;
- route;
- NBTscan;
- Certutil;
- Port Scanner.
These tools help attackers imitate innocuous daily activities, avoid leaving traces in logs, and avoid the attention of defense mechanisms and products.
The researchers say that the new attacks were linked to Billbug, as the attackers used two custom backdoors, already known to experts on past group attacks, as part of this campaign: Hannotog and Sagerunex.
Hannotog’s features include: changing firewall settings to allow any traffic, creating a persistent presence on the system, downloading encrypted data, executing CMD commands, and downloading files to the victim’s device.
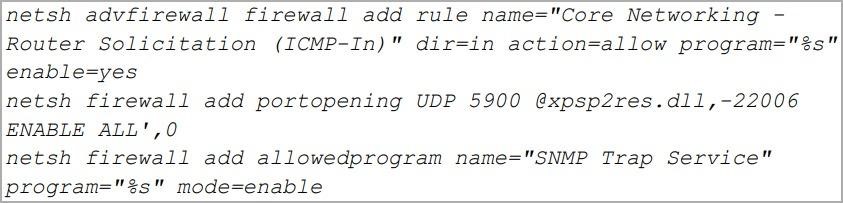
Hannotog changes firewall settings
Sagerunex, in turn, is loaded into the Hannotog system and injected into the explorer.exe process. It then writes the logs to a temporary local file encrypted with AES (256-bit). The configuration and state of the backdoor is stored locally and encrypted using RC4, and the keys for both programs are hardcoded in the malware itself.