Researchers from the Avast IoT Lab have discovered serious vulnerabilities in two popular set-top boxes from Thomson and Philips. Found vulnerabilities allow storing malware on devices, allowing attackers to use devices in botnets, as well as to carry out ransomware attacks using them.
Bugs were found in THOMSON THT741FTA and Philips DTR3502BFTA devices, which are widespread in European countries and popular with consumers, whose TVs do not support the DVB-T2 standard, which provides access to HD resolution.The experts contacted Philips and Thomson, informing them of the research findings and proposing a number of measures to improve product safety. Unfortunately, Philips said the vulnerabilities could no longer be fixed, and Thomson did not respond to Avast’s message at all.
The investigation, which began back in January of this year, led Vladislav Ilyushin, head of the IoT laboratory, and IoT threat researcher Marko Zbirka. This research was part of an Avast initiative to research and test security solutions for smart devices.
Let me remind you that recently the staff of this IoT laboratory recorded more than 500,000 attacks on iOT-devices in 2 hours.
At the beginning of the analysis, the experts discovered that both manufacturers supply STBs with Telnet ports open by default.
“This protocol was created in 1969, so it is more than 50 years old, it does not have encryption, but is still used to communicate with remote devices or servers. Essentially, in the case of vulnerable set-top boxes, Telnet allows attackers to remotely access devices and make them part of botnets, then use them for DDoS attacks and other malicious activity”, – say the Avast experts.
For example, the researchers managed easily run the binary file of the famous IoT Mirai malware on both consoles.
Also, experts have identified a problem related to the architecture of gadgets. So, both consoles use the Linux kernel version 3.10.23, installed on devices back in 2016. In essence, it serves as a bridge between the hardware and software of the set-top boxes, but support for version 3.10.23 expired back in November 2017. After this date release of updates stopped, and as a result, users are now vulnerable to potential attacks for which they simply did not receive fixes.
In addition to the already listed problems, an unencrypted connection was found in Philips and Thomson consoles between the set-top boxes and the pre-installed (and outdated) application of the popular weather forecast service AccuWeather.
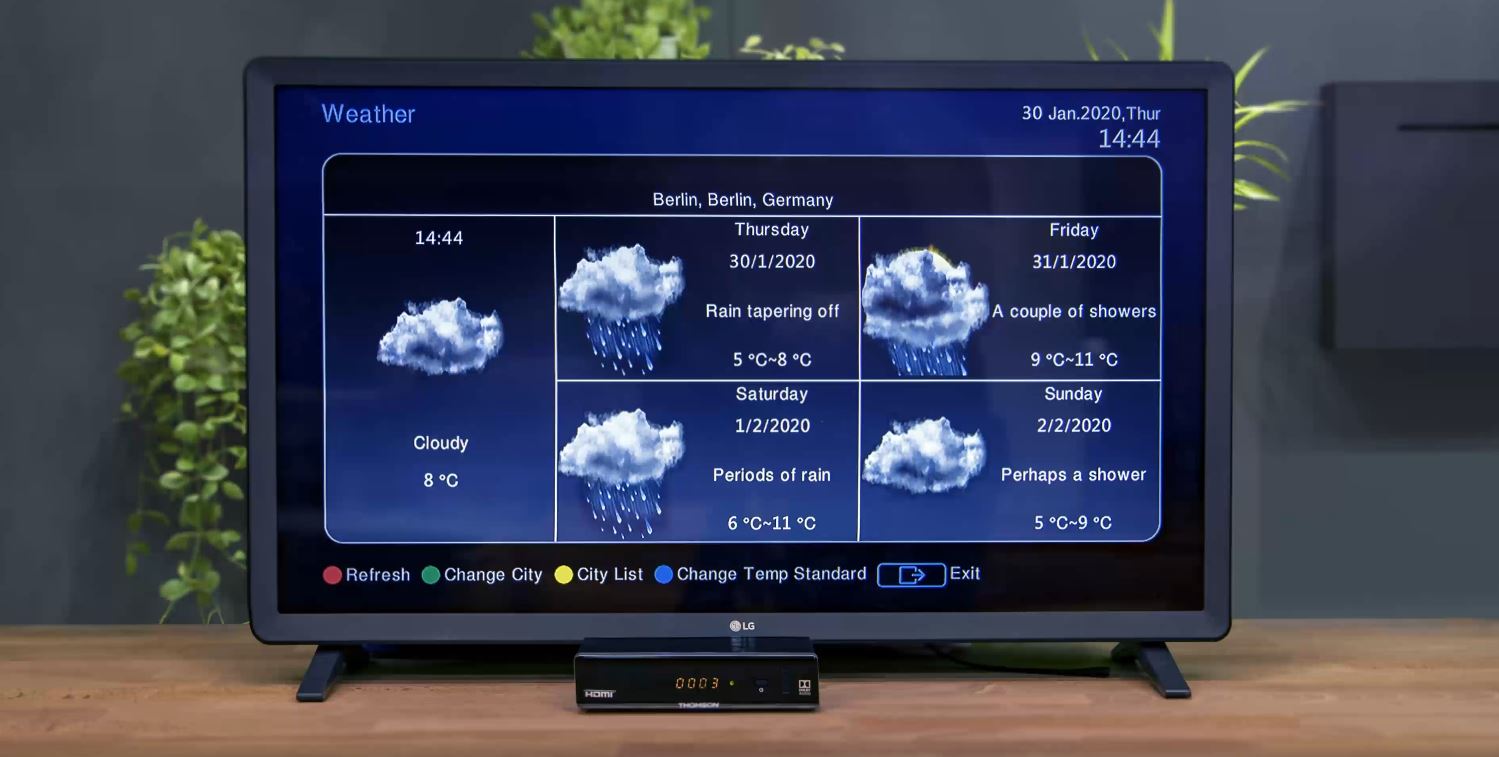
An insecure connection between set-top boxes and the AccuWeather backend allows an attacker to change the content that users see on their TVs when using the weather app. For example, an attacker might display a ransomware message on the screen stating that the user’s TV has been hacked and now requires a ransom payment to unblock it.
“Manufacturers are responsible for meeting safety standards not only when they sell them. They are also responsible for the safety of their further exploitation by users. Unfortunately, manufacturers of IoT devices rarely wonder how they can mitigate the threats posed by their products. Instead, they rely on minimal or at least completely ignore IoT security to cut costs and speed time to market”, – said in Avast.
As a result, Avast experts recommend that users of DVB-T2 set-top boxes choose models from reliable brands that have a history of long-term support for devices and work on security. In addition, after purchase, it is worth disabling the Plug and Play (UPnP) settings, and also checking the port forwarding configuration and disabling it, if it is not necessary. If the user still has doubts about the reliability and safety of such a device, it is worth abandoning the “smart” functions at all and not connecting the device to the home network.
As a reminder, Avast researchers recently found several surveillance applications on Google Play.





