Hundreds of Apps and Websites Affected by Malicious NPM Packages
About two dozen malicious NPM packages have been stealing data from forms embedded in mobile apps and websites since December 2021.
Experts gave this campaign the name IconBurst, since the malware was mostly disguised as popular ionic packages.Let me remind you that we also said that Hackers Stole the Credentials of 100,000 npm Users.
A new malware campaign was discovered by ReversingLabs researchers, who say that the infected packages contained obfuscated JavaScript, which stole data from all kinds of forms (including those used for login).
The malicious packages, most of which have been published in recent months, have collectively been downloaded more than 27,000 times. The full list can be seen below.
| Author/Package Name | Number of downloads |
| fontsawesome | |
| ionic-icon | 108 |
| ionicio | 3724 |
| ionic-io | |
| icon-package | 17 774 |
| ajax-libs | 2440 |
| umbrellaks | 686 |
| ajax-library | 530 |
| arpanrizki | |
| iconion-package | 101 |
| package-sidr | 91 |
| kbrstore | 89 |
| icons-package | 380 |
| subek | 99 |
| package-show | 103 |
| package-icon | 122 |
| kbrstore | |
| icons-packages | 170 |
| ionicon-package | 64 |
| icons-pack | 49 |
| pack-icons | 468 |
| ionicons-pack | 89 |
| aselole | |
| package-ionicons | 144 |
| package-ionicon | 57 |
| base64-javascript | 40 |
| ionicons-js | 38 |
| ionicons-json | 39 |
| footericon | |
| footericon | 1,903 |
| ajax-libz | |
| roar-01 | 40 |
| roar-02 | 37 |
| wkwk100 | 38 |
| swiper-bundie | 39 |
| ajax-libz | 40 |
| swiper-bundle | 185 |
| atez | 43 |
| ajax-googleapis | 38 |
| tezdoank | 69 |
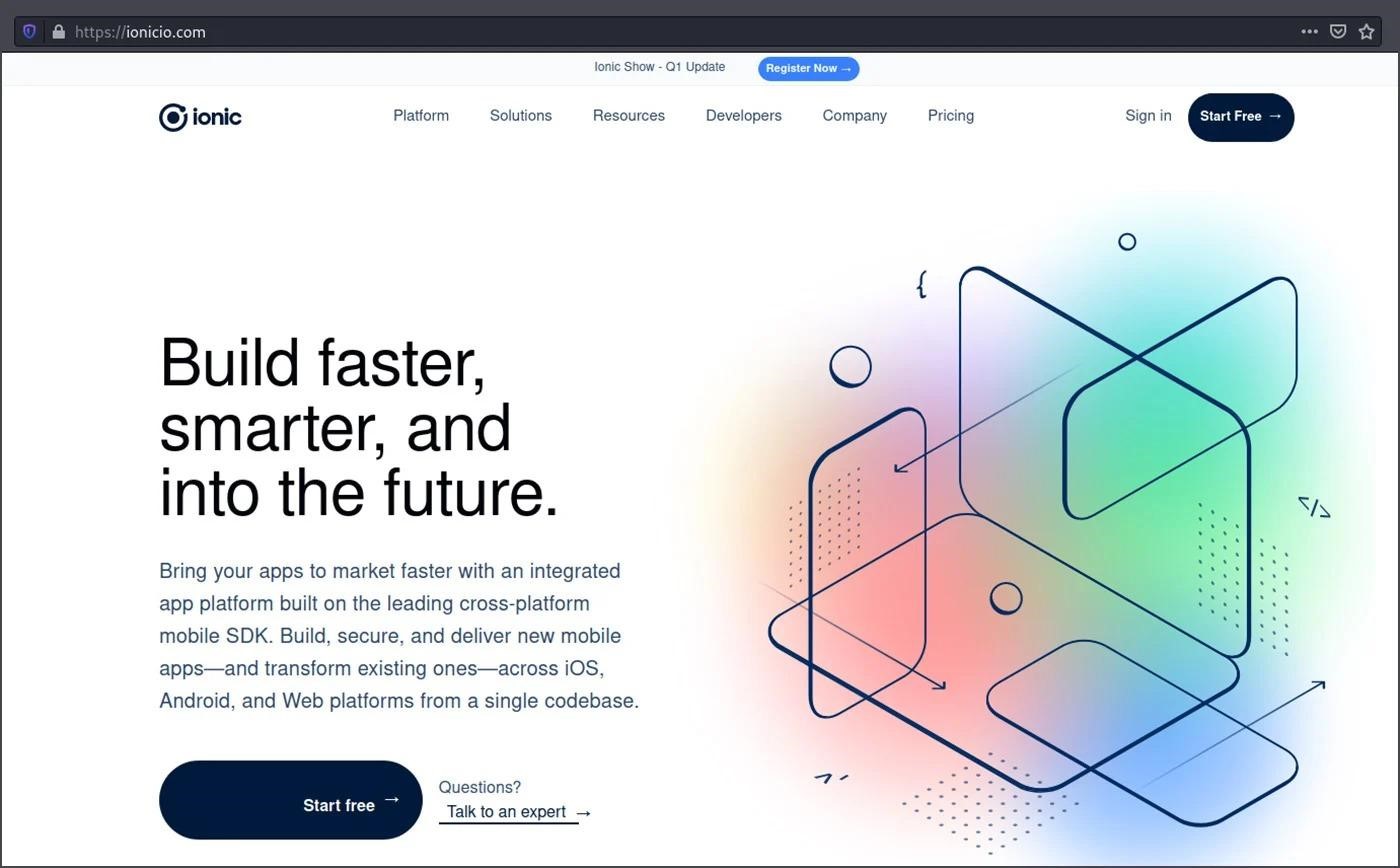
ReversingLabs analysts noticed that data stolen by icon-package was redirected to the ionicio[.]com domain. And the site hosted at this address was specially created in such a way as to resemble the real ionic[.]io resource. At the same time, it is noted that the similarities between the domains used to steal data suggest that the entire campaign is controlled by the same attackers.
ReversingLabs notified the NPM security team of its discovery as early as July 1, 2022, however it is reported that some IconBurst malware packages are still available in the repositories.