US police arrest Latvian citizen suspected of developing TrickBot
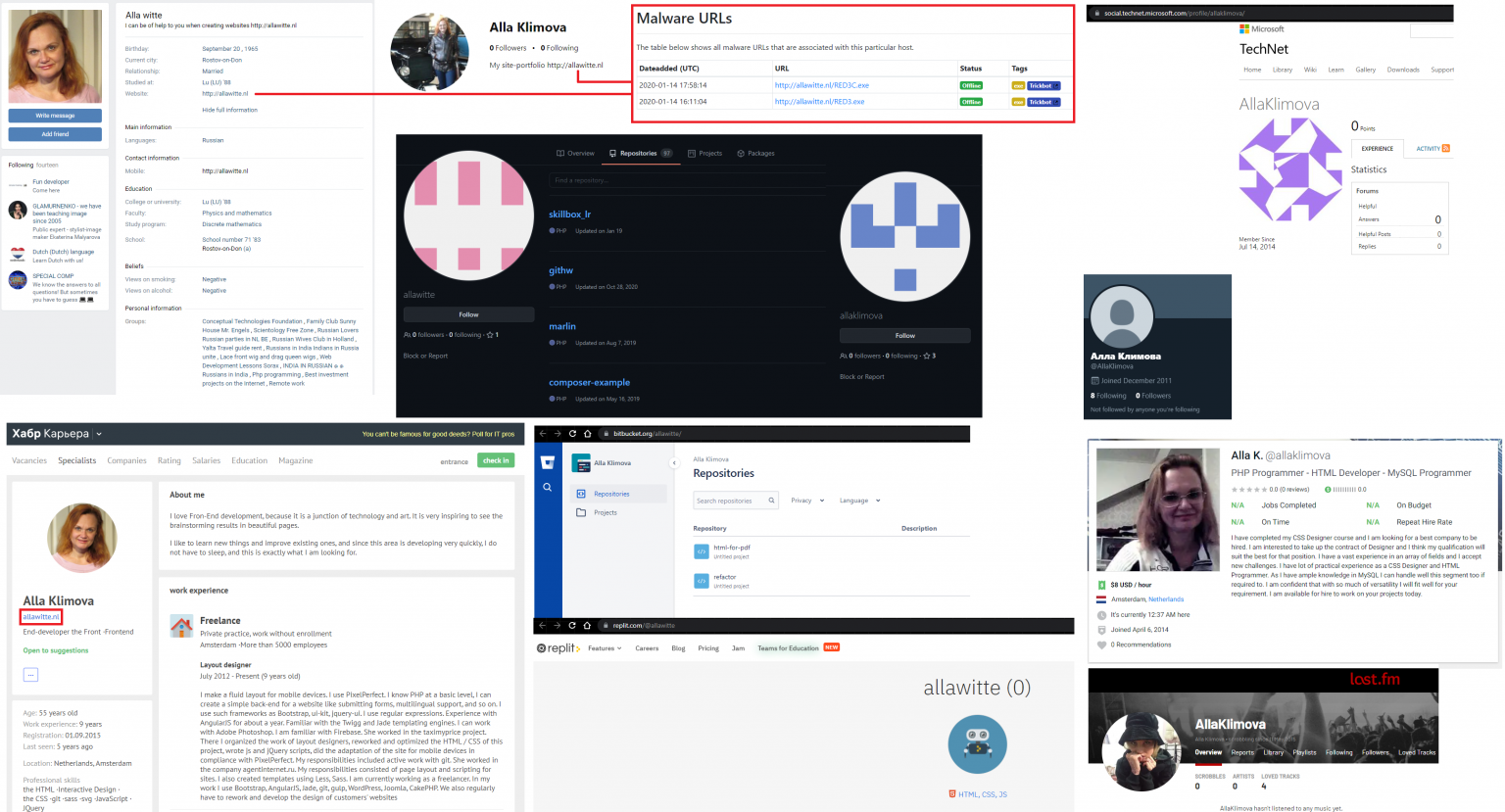
The US Department of Justice announced the arrest of 55-year-old Latvian citizen Alla Witte, who is suspected of developing TrickBot.
The woman is believed to have been part of the TrickBot malware development team, where she wrote code to manage malware and deploy ransomware on infected machines.Witte was arrested back on February 6, 2021 in Miami, Florida. According to the investigation, the woman was known on the network under the nickname Max and had been cooperating with the creators of TrickBot from the very beginning, that is, since November 2015 (when the remnants of the Dyre hack group created a new version of same-named the malware and then renamed it TrickBot).
According to court documents, Witte is one of 17 possible developers of TrickBot. Law enforcers believe that Witte was responsible for the following aspects of the malware: creating code related to monitoring and tracking authorized Trickbot users; ransomware control and deployment; receiving payments from victims; developing tools and protocols for storing stolen credentials.
Witte is the first person arrested for participating in the development of TrickBot. US officials say other suspects are still stay in Russia, Belarus, Ukraine and Suriname.
The woman was charged on 19 counts, and the cybersecurity community is discussing that Witte did not seem to be too eager to hide her identity and even posted versions of TrickBot that were in earnings on her personal website.
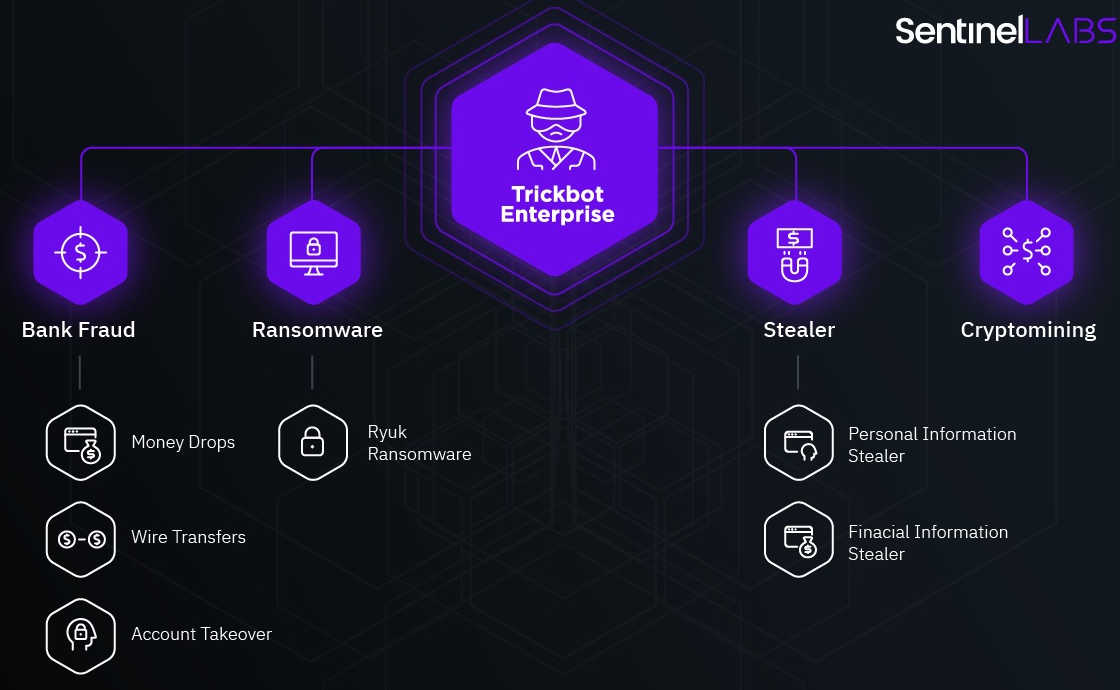
TrickBot is one of the largest and most successful recent malware threats. Malware was first spotted back in 2015, shortly after a series of high-profile arrests that significantly changed the composition of the Dyre hack group.
Over the years, malware has evolved from a classic banking Trojan designed to steal funds from bank accounts to a multifunctional dropper that spreads other threats (from miners to ransomware and info-stealers).
In the fall of 2020, a large-scale operation was carried out aimed at eliminating TrickBot. It was attended by law enforcement agencies, specialists from the Microsoft Defender team, the non-profit organization FS-ISAC, as well as ESET, Lumen, NTT and Symantec.
At that time, many experts wrote that although Microsoft was able to disable the TrickBot infrastructure, most likely the botnet will “survive” and eventually its operators will put into operation new control servers and continue their activity. Unfortunately, this is what happened.