Researchers Find Out Most SS7 Hacking Suggestions Are Scams
SOS Intelligence has examined the darknet for proposals to hack SS7 and found 84 unique .onion domains that advertised such services, but it turned out that scammers were simply hiding behind these sites.
Let me remind you that the existence of vulnerabilities in the Signaling System 7 protocol (SS7, Shared signaling channel No. 7, OKS-7) became known back in the mid-2010s, and soon the first attacks on these problems were officially recorded. Besides SMS interception and spoofing, vulnerabilities in SS7 can be exploited to intercept or forward calls, 2FA codes, locate devices, and more.Of course, many cybercriminals are interested in such services, and SOS Intelligence analysts decided to find out what the SS7 hacking market is. Finding 84 unique .onion domains offering such services, the researchers quickly reduced the sample to active sites and obtained just four resources: SS7 Exploiter, SS7 ONLINE Exploiter, SS7 Hack, and Dark Fox Market.
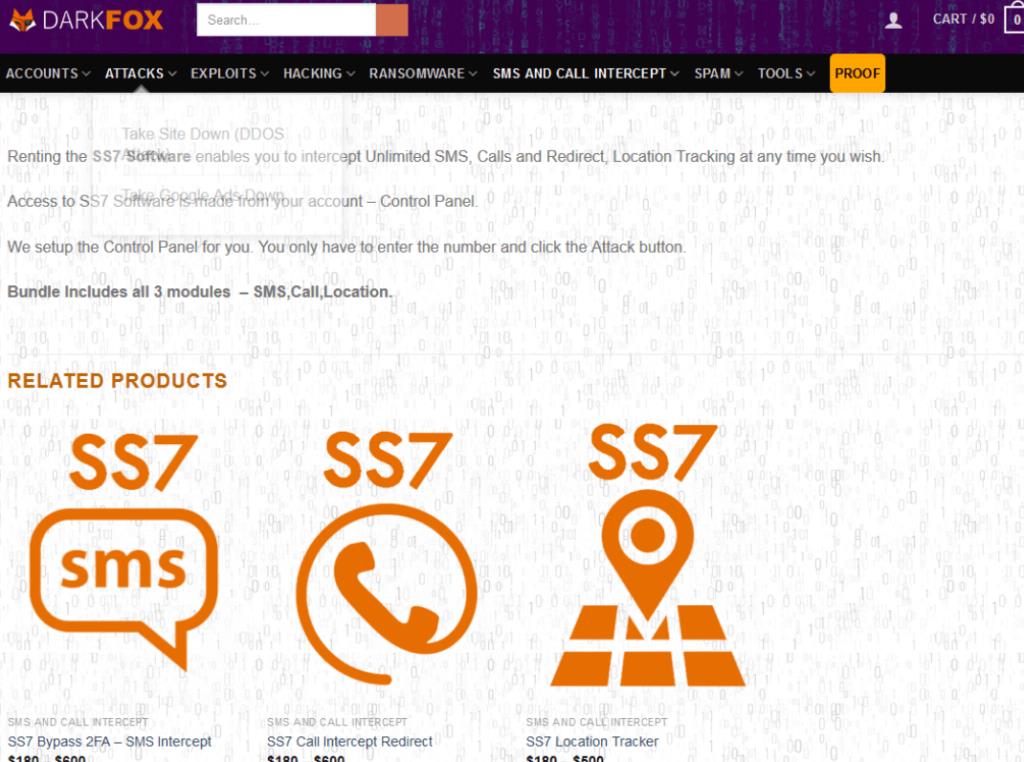
All four sites claimed that their operators offer services for intercepting and forging SMS, tracking location, and intercepting and redirecting calls.
However, experts have noticed that the sites look isolated and do not have a lot of external links.
Having tried to use the set of exploits offered by the resource for SS7 (in the hope of mirroring the API), the researchers did not achieve any result, since the service was disabled.
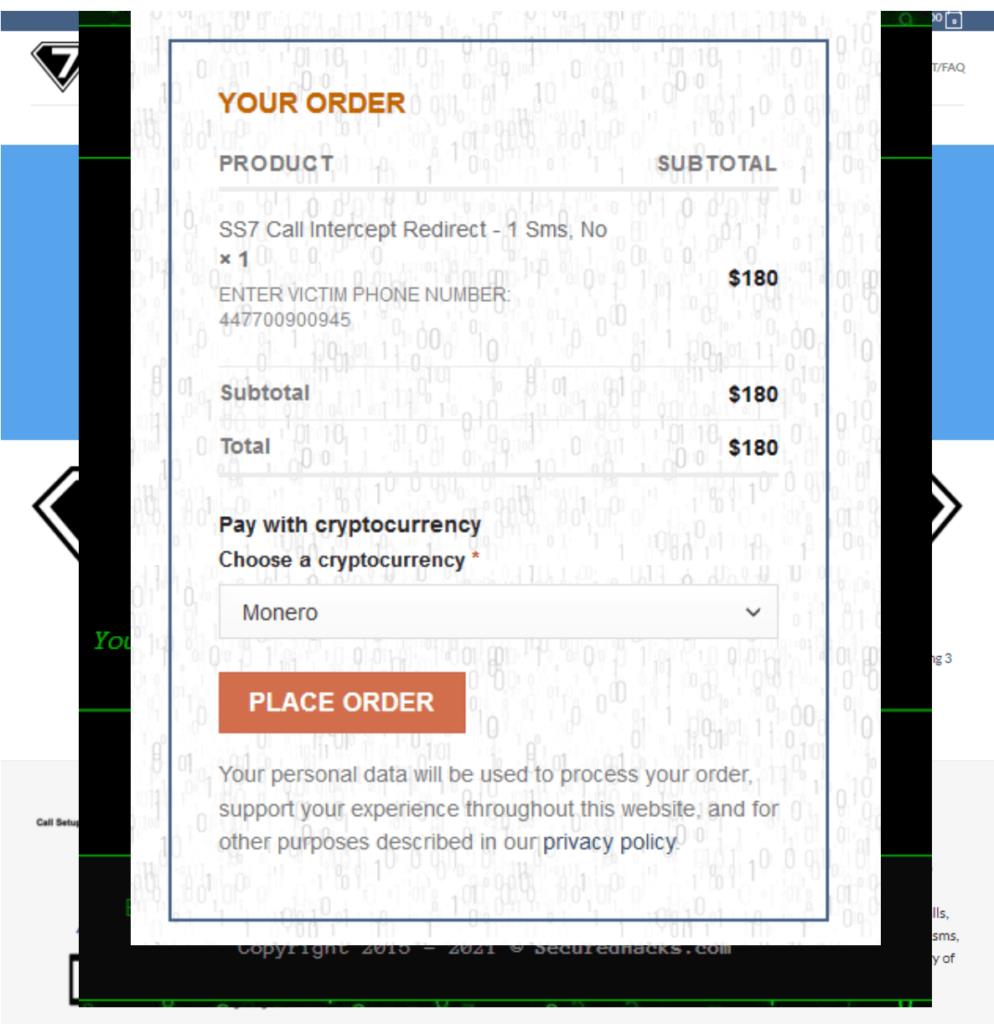
On the Dark Fox Market platform, which charges $ 180 for each targeted phone number, researchers generally found demo videos uploaded by Russian users to YouTube back in 2016. Most likely, these videos were simply stolen from YouTube and had nothing to do with Dark Fox Market, which does not offer a working SS7 hacking service anyway.
Alas, after examining the cryptocurrency wallets of the operators of these sites, SOS Intelligence experts discovered that fraudsters make a lot of money by hacking SS7.





