More Than 12% of Online Stores May Accidentally “Merge” Personal Data and Backups
According to a study conducted by Sansec, many online stores mistakenly leave private backups in the public domain (for example, store them in public folders), which may contain passwords from internal accounts and other non-public information.
As a result, all this can be used to capture e-commerce sites and extortion.Let me remind you that we also wrote that The operator of an online store selling stolen bank cards sentenced to 7.5 years in prison, and also that Privacy-focused ClearURLs extension removed from Chrome Web Store.
Also, the media, for example, indicated that Magento Store Owners Intentionally Bypass Critical Vulnerability Patch.
Analysts studied 2037 online stores of various sizes and found that 250 (12.3%) of them store ZIP, SQL and TAR archives in public web folders that can be freely accessed without any authentication.
It seems that the archives are located where they do not belong at all, due to banal negligence, human error, or by mistake.
Even worse, these archives are often backups that contain database passwords, secret administrative URLs, internal API keys, and customer personal data.

In the same report, the researchers highlight that they are seeing constant activity from attackers who use automatic scanning to find such backups and hack them.
At the same time, the criminals sort through various combinations of possible backup names on the target sites, based on the name of the resource and public DNS data, for example, /db/staging-SITENAME.zip. Since such “probes” are inexpensive for hackers and do not affect the performance of the target resource, attackers can conduct such reconnaissance for several weeks until they find what they are looking for.
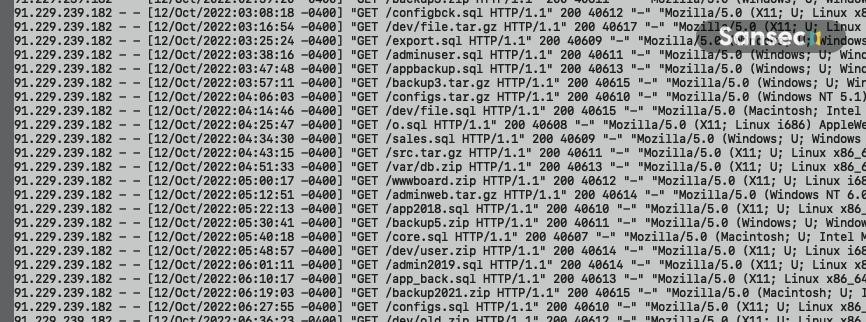
Sansec reports that such attacks come from many IP addresses, which means that hackers are well aware of the existence of backups forgotten in the public domain, and purposefully try to use them.