How to uninstall Identity Protector
Identity Protector is a security app from rogue software family. When installed on the your PC, this program runs continuous task-bar warnings and notifies specifying that your system has lots of errors or viruses. What is scarier is its ambition to misinform users by exaggerating the scan report showing a variety of infections or danger files.
By utilizing variations of strategy, Identity Protector can get inside the PC anonymously. You will just realize about the invasion when this rogue program begins to scan the computer. It uses frightening tactics by releasing bunch of incorrect detection, that includes malware existence, start-up mistakes, missing out on files, windows registry errors, and a lot more difficulties. This false information tactic by Identity Protector plans to encourage victims that registered variation is required to perform fast tidy up of the infected computer.
Identity Protector scan your computer registry for these outdated entries and offer to remove them. Because there are a lot of computer system registry entries to go through, this tool might in some cases likewise remove useful pc registry entries, triggering you issues. The Internet is full of stories from people who have actually run a windows registry cleaner and came across issues. In a finest case circumstance, Identity Protector will eliminate a couple of hundred unneeded entries and lower the size of your windows registry by a few kilobytes. This makes no distinction in noticeable efficiency.
Identity Protector is bundled with other free software application that you download off of the Web. Sadly, some complimentary downloads do not effectively disclose that other software will likewise be installed and you may discover that you have actually installed adware without your knowledge.

You must always focus when setting up software because frequently, a software application installer includes optional installs. Be very careful what you agree to install.
Always select the custom setup and deselect anything that is not familiar, especially optional software application that you never ever wished to download and install in the first location. It goes without stating that you need to not set up software application that you do not trust.
How to remove Identity Protector (Uninstall Guide)
To remove the Identity Protector, follow these steps:
STEP 1: Uninstall Identity Protector from Windows
STEP 2: Use GridinSoft Anti-Malware to remove the Identity Protector
STEP 3: How to protect your PC from Identity Protector
The easiest method to remove Identity Protector is to run an anti-malware program capable of detecting adware in general and Identity Protector in particular. You may try GridinSoft Anti-Malware. It’s good at detecting and removing adware and other unwanted programs
STEP 1: Uninstall Identity Protector from Windows
Go to Programs and Features, uninstall suspicious programs, programs you don’t remember installing, or programs you installed just before Identity Protector appeared on your browser for the first time. When you are not sure if a program is safe, look for the answer on the Internet.
Windows XP:
- Click Start.
- In the Start menu select Settings => Control Panel.
- Find and click Add or Remove Programs.
- Select Identity Protector.
- Click Remove.
Windows Vista:
- Click Start.
- In the Start menu select Control Panel.
- Find and click Uninstall a program.
- Select Identity Protector.
- Click Uninstall.
Windows 7:
- Click Start.
- In the Start menu select Control Panel.
- Find and select Programs and Features or Uninstall a program.
- Select Identity Protector.
- Click Uninstall.
Windows 8 / Windows 8.1:
- Press and hold Windows key
 and hit X key.
and hit X key. - Select Programs and Features from the menu.
- Select Identity Protector.
- Click Uninstall.
Windows 10:
- Press and hold Windows key
 and hit X key.
and hit X key. - Select Programs and Features from the menu.
- Select Identity Protector.
- Click Uninstall.
STEP 2: Use GridinSoft Anti-Malware to remove the Identity Protector
1.Download GridinSoft Anti-Malware.
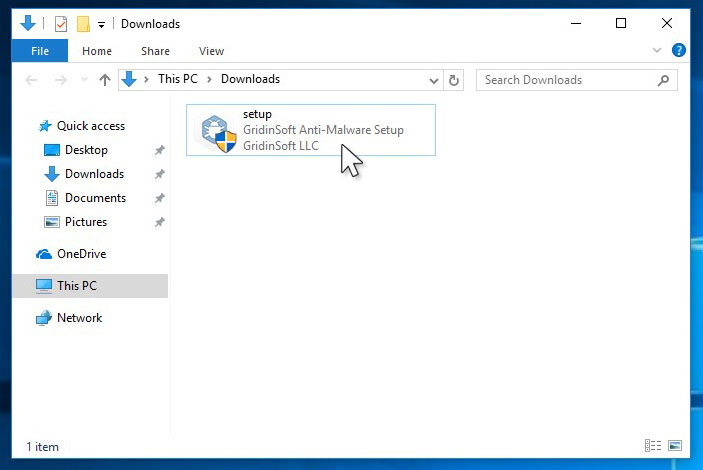
2. Double-click on the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-ag.exe file to install GridinSoft Anti-Malware on your computer.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
3. Press Install button for run GridinSoft Anti-Malware.
3.Once installed, GridinSoft Anti-Malware will automatically run.
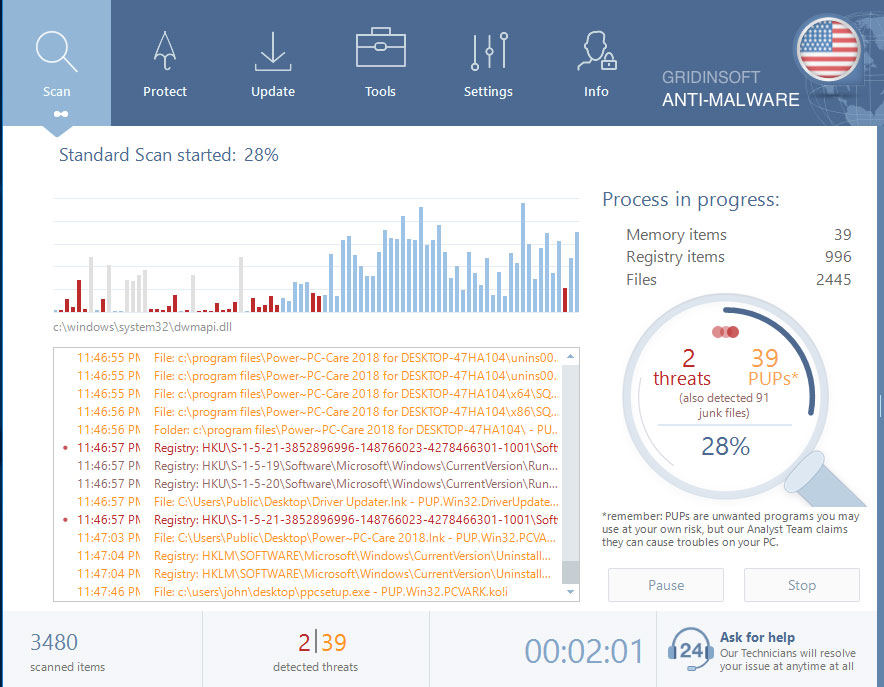
4. Wait for the GridinSoft Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your computer for Identity Protector and other malicious programs. This process can take a 20-30 minutes, so we suggest you periodically check on the status of the scan process.
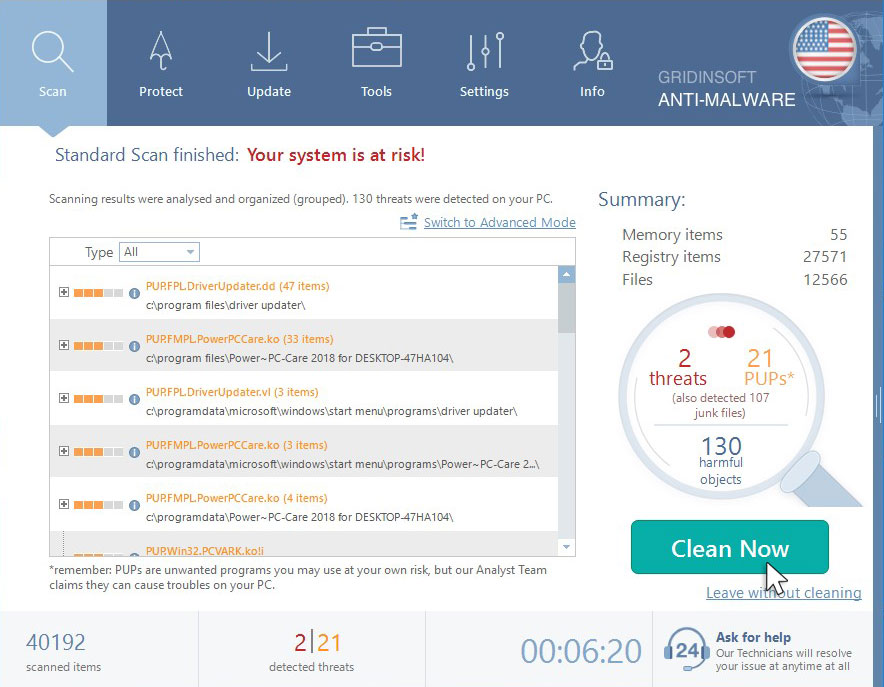
5. Click on “Clean Now”.
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
STEP 3: How to Protect Your PC From Identity Protector
- Get a powerful anti-malware software application, capable of identifying and eliminating PUPs. Having several on-demand scanners would certainly be a great suggestion as well.
- Maintain Windows firewall program allowed or get a third-party one.
- Keep your OS, internet browsers as well as safety energies upgraded. Malware developers discover brand-new browser and also OS susceptabilities to make use of constantly. Software writers, subsequently, launch patches and also updates to remove the known susceptabilities as well as minimal the opportunity of malware penetration. Antivirus program’s trademark data sources obtain upgraded each day and much more often to include brand-new infection signatures.
- Readjust your browsers’ setups to block pop-ups and also to fill plug-ins only when clicked.
- Download and install as well as utilize Adguard, uBlock Origin, Adblock or Adblock Plus browser extension/add-on to obstruct third-party promotions on web-sites.
- Don’t just click any kind of link you see while browsing the internet. That uses specifically to web links in comments, on forums, or in instantaneous messengers. Pretty frequently these are spam web links. Occasionally they are utilized for boosting the traffic to websites, but usually adequate they will land you on web pages that will try to implement a malicious code and also contaminate your computer. Links from your good friends are suspicious as well: the individual who shares an adorable video could not understand that the page includes intimidating manuscript.
- Don’t download software application from unproven web-sites. You can easily download and install a trojan (malware that claims to be an useful application); or some unwanted programs could obtain installed in addition to the application.
- When mounting free software or shareware, be reasonable as well as don’t rush via the procedure. Pick Custom or Advanced setup mode, try to find checkboxes that request for your permission to mount third-party applications and also uncheck them, read End User License Agreement to see to it nothing else is going to obtain installed. You can make exceptions for the apps you know and count on, certainly. If declining from installing unwanted programs is not feasible, we encourage you to cancel the setup completely.