Hackers exploit coronavirus vaccine theme
We have already talked about the avalanche-like increase in usage of COVID-19 topics by cybercriminals. But now, Check Point experts have warned of a new trend: now hackers are exploiting the topic of a coronavirus vaccine.
The main vector of attacks is email, which accounted for 82% of such attacks in the last 30 days.
“Almost every such letter contains malicious links. After clicking on such a link, victims download a malicious file, usually in the .exe, .xls or .doc format”, – say the experts.
Check Point researchers share two examples of such malicious emails.
In the first example, malicious spam was spread through emails with the subject “URGENT INFORMATION LETTER: COVID-19 NEW APPROVED VACCINES”. Such emails contain malicious .EXE files named “Download_Covid 19 Newly Approved Vaccines 07.23.2020.exe”, which ultimately installs an info-stealer, which is capable of stealing victim’s information, including credentials.
In the second example, emails are sent with the subject “UK coronavirus vaccine effort is progressing badly appropriate, recruiting consequence and elder adults”. Such messages contain a malicious link – surgicaltoll.comvy2g4b.html, which currently appears to be inactive.
Investigation revealed that the link was used to redirect traffic to a medical-themed phishing site thelifestillgoeson[.]Su, which was trying to mimic a Canadian pharmacy.
However, experts note that overall, the number of coronavirus-related attacks in July significantly dropped. For example, in July, researchers detected about 61,000 COVID-19 attacks every week, which is 50% less than the weekly average in June (about 130,000 attacks).
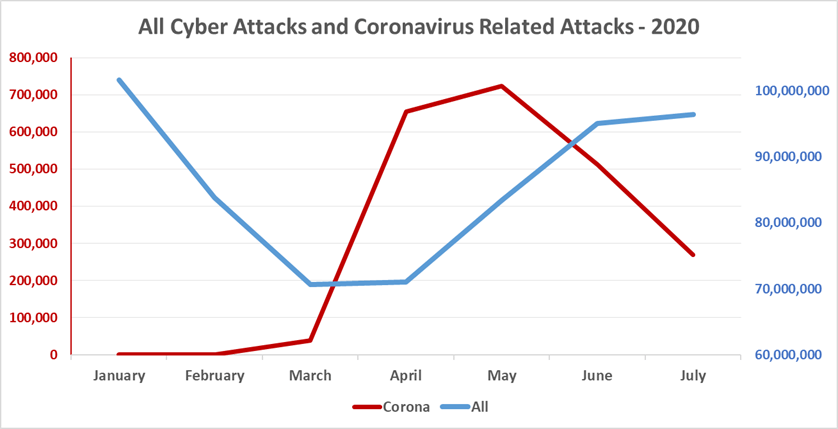
At the same time, the number of new domains associated with coronavirus and vaccines against it doubled in June and July 2020. Analysts estimate that every 25 pages on malicious COVID-19 websites are now associated with vaccines.
“Lately, we’ve seen hackers exploit people’s fear and interest in COVID-19 vaccines. In the majority of campaigns is used victim’s mail. 80% of attacks on organizations start with a malicious email. These attacks use the weakest factor — the human factor. This means that employee mailboxes are the weakest link in organizations”, — says Check Point specialist Omer Dembinski.
Check Point urges everyone carefully read the subject line of incoming emails. If they have the word “vaccine” in them, think twice. Most likely, they want to get the most important information from you.
The pandemic has become a favorable environment for spreading of viruses (sorry, for the pun) and great opportunity for cybercriminals to make money. Some even attacked the real developers of the COVID-19 vaccines. Be physically healthy and take care of your computer systems and networks.