Over 100 Dell Models At Risk Due to BIOSConnect Vulnerabilities
Eclypsium has discovered a number of vulnerabilities related to the BIOSConnect function (provides remote firmware update and OS recovery functions), which is part of the Dell SupportAssist utility.
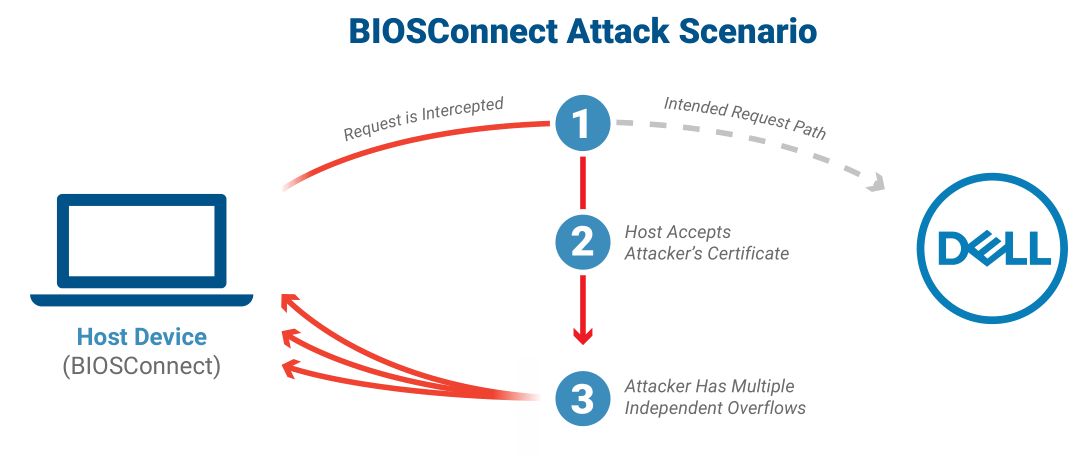
The problem is that we are talking about millions of PCs, laptops and tablets, as the utility is preinstalled on most Dell computers.The vulnerability chain discovered by Eclypsium researchers scored 8.3 out of 10 on the CVSS vulnerability rating scale. The issue allows privileged remote attackers to impersonate Dell.com (through a Machine-in-the-Middle attack) and take control of the boot process by delivering a malicious update to the target device.
Researchers identified one issue leading to an insecure TLS connection from BIOS to Dell (CVE-2021-21571) and three overflow vulnerabilities (CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574). Two flaws affect the OS recovery process, and another bug affects the firmware update process. As a result, each of the problems can lead to the execution of arbitrary code in the BIOS.
It is estimated that approximately 30,000,000 devices are affected. An attacker can control the boot process of the host operating system and disable protection to remain undetected. This will allow him to gain a foothold in the system, while having the highest privileges on the device.
According to Eclypsium, users will have to update the BIOS/UEFI of all affected devices. Experts also recommend using an alternative method (not BIOSConnect) for applying BIOS updates.
Dell is already releasing BIOS/UEFI updates for affected machines and executable patches on Dell.com. So, CVE-2021-21573 and CVE-2021-21574 do not require additional actions from the user, since they were eliminated on the server side back in May 2021.
However, to fix CVE-2021-21571 and CVE-2021-21572, users need to update the BIOS.
Users who are not yet able to update their systems can disable BIOSConnect from the BIOS setup page or Dell Command | Configure (DCC).
Let me remind you that we wrote that Cybersecurity experts discovered the second ever bootkit for UEFI.