Cozy Bear hack group is still active and attacks European foreign ministries
The Russian-speaking hacker group Cozy Bear (aka APT29 and Dukes) was considered very active from 2014 to 2017, but as ESET experts found out, this cybercriminal group is still active and attacks governmental structures.
These hackers were accused of hacking the National Committee of the Democratic Party of the United States in anticipation of the 2016 elections, as well as of numerous attacks on various governmental departments in Europe and beyond.According to information security experts, this group allegedly works with the Russian FSB (security service) and was also involved in attacks on the US White House postal system, the US Department of Foreign Affairs and the Joint Chiefs of Staff.
However, in recent years, almost nothing has been heard about Cozy Bear, apart from a one-time incident in November 2018 related to a phishing campaign aimed at several American organizations. Because of this, information security experts believed that the group may have ceased to exist, but now ESET experts have found that this is far from truth.
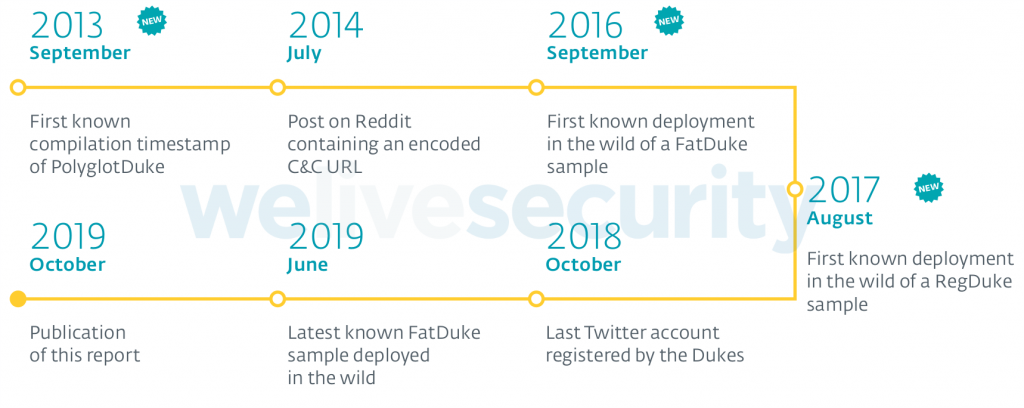
Researchers immediately identified three new families of malware created by Cozy Bear: PolyglotDuke, RegDuke and FatDuke, as well as the previously documented MiniDuke backdoor, which has been updated. Until recently, these tools were used by cybercriminals, and the last sample observed by experts was deployed in June 2019.
Read also: Europol called the main cyberthreats of 2019
Here’s how ESET experts describe the actions of a PolyglotDuke, which uses Twitter or other websites such as Reddit and Imgur to get its C&C URL. It also relies on steganography in images for its C&C communication.
RegDuke, a recovery first stage, which uses Dropbox as its C&C server. The main payload is encrypted on disk and the encryption key is stored in the Windows registry. It also relies on steganography as above.
MiniDuke backdoor, the second stage. This simple backdoor is written in assembly. It is very similar to older MiniDuke backdoors.
FatDuke, the third stage. This sophisticated backdoor implements a lot of functionalities and has a very flexible configuration. Its code is also well obfuscated using many opaque predicates. They re-compile it and modify the obfuscation frequently to bypass security product detections.
“Dukes have been quite active since 2016, developing new implants and compromising high-value targets. We call these newly uncovered Dukes activities, collectively, Operation Ghost”, — write in ESET.
ESET experts believe that the “Operation Ghost” began in 2013 and continues till this day. During this time, the group attacked at least three European foreign ministries, as well as the US embassy of an unnamed EU country in Washington.
Cozy Bear used a variety of online services to manage their malware, including Twitter, Imgur and Reddit, and also resorted to steganography. So, in one of the examples described by the researchers, the payload of the malware was hidden among the metadata of the practically unchanged PNG file.
Analysts write that it is impossible to completely exclude the possibility that this activity comes not from Cozy Bear, but from someone, who is conducting operations under a false flag. However, the involvement of APT29, in particular, is indicated by the fact that this malicious campaign was launched simultaneously with other attacks of the group and began at a time when only a small part of the arsenal of hackers was known to researchers.
“They are very persistent. They steal credentials and use them systematically to move laterally on the network. We have seen them using administrative credentials to compromise or re-compromise machines on the same local network”, — report in ESET.
A list of indicators of compromise has already been published on GitHub, and researchers have also prepared a detailed report detailing all the technical aspects of the new Cozy Bear tools.
When responding to a Dukes compromise, it is important to make sure to remove every implant in a short time. Otherwise, the attackers will use any remaining implant to compromise the cleaned systems again.






One Comment