Chinese hackers used NSA exploit years before The Shadow Brokers leak
In 2017, the group The Shadow Brokers stole the NSA hacking toolkit and tried to sell it for a long time, but it turns out that Chinese hackers used the NSA exploit several years before the leak.
When no buyers were found, The Shadow Brokers published most of the dump for free in the public domain.Many will probably remember that at that time, among other things, the exploits ETERNALBLUE and DOUBLEPULSAR became public and were used to attack a vulnerability in SMB to spread the well-known ransomware WannaCry.
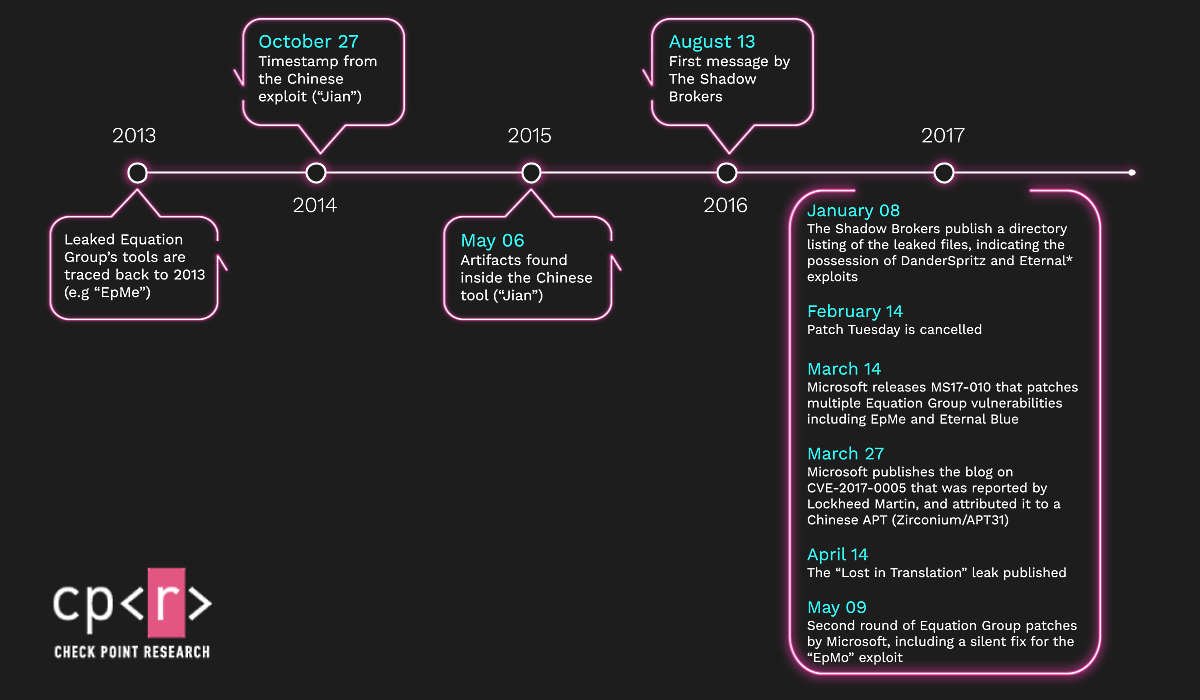
Now, Check Point researchers have noticed that the Chinese hack group APT31 (aka Zirconium) used an exploit for the Windows vulnerability CVE-2017-2005 three years before The Shadow Brokers “leaked” this tool to the public. along with other exploits and data stolen from the NSA.
The Chinese hacker exploit is named Jian. It is a copy of the EpMe exploit, which was developed and actively used from 2014 to 2017 by hackers from the Equation Group (whose activities experts have long linked directly to the NSA). When The Shadow Brokers stole NSA data and tools and then made it public, EpMe went public as well. However, it fell into the hands of the Chinese much earlier.
“To our surprise, we discovered that the APT31 exploit is actually a reconstructed version of the Equation Group exploit called EpMe. This means that the Equation Group exploit was used by a Chinese group, most likely against targets in the United States”, — the researchers write.
Both tools were used to elevate privileges in the local Windows environment. Let me remind you that Microsoft fixed the CVE-2017-0005 vulnerability, which Jian and EpMe abused, but only after Lockheed Martin discovered a working exploit and provided it to Microsoft experts.
This is not the first time that attackers have used Equation Group tools in their attacks, but the first time that hackers have somehow managed to get exploit samples and clone them for their own purposes.
The researchers recall that the APT3 group had previously used their own version of the EternalSynergy tool (called UPSynergy). However, then information security experts from Symantec came to the conclusion that the hackers had recreated the exploit from the intercepted network traffic and did not have the source code on hand.
In turn, APT31 somehow managed to obtain of all versions of the NSA exploit, since Jian was built using 32-bit and 64-bit versions of the EpMe tool. Check Point believes that information could get into the hands of Chinese hackers in several ways:
- during the Equation Group’s network operation against some Chinese target;
- during the work of Equation Group in a third-party network, which was also controlled by Chinese hackers;
- during an attack on the Equation Group infrastructure.
“Our study is a clear demonstration of how one APT uses the tools of another APT for its own operations, which makes it difficult for information security researchers to accurately attribute attacks, and also demonstrates how complex reality is and how little we know”, — summarize Check Point analysts.
Let me remind you that we talked about the fact that Shadow Brokers archive allowed tracing mysterious DarkUniverse group. We also reported that During the analysis of one of hackers ’attacks, experts discovered traces of multiply Chinese government cyberoperations.