Researchers Hacked License Plates Powered by E-Ink
Last fall, California allowed the use of digital license plates that run on electronic ink (e-ink). Less than six months later, researchers have already discovered vulnerabilities in this system that allow each license plate to be tracked, reprogrammed or erased.

Let me remind you that we also wrote that Hackers Who Sold Car Hacking Tools with Keyless Entry Arrested, and also that DoppelPaymer operators published in the public domain Tesla documents.
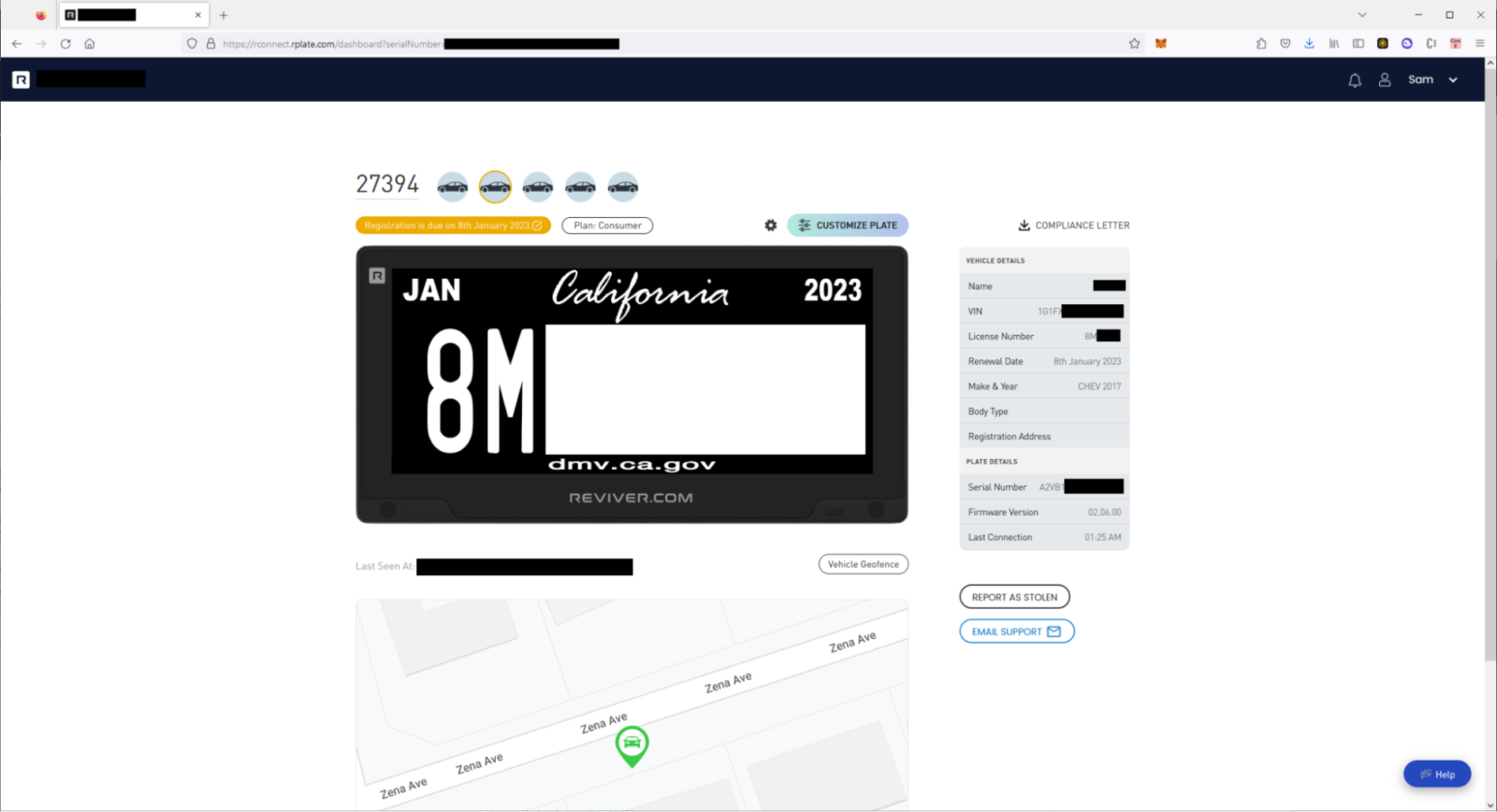
One of the studies by Curry and his friends was devoted to modern digital numbers, the only major manufacturer of which is the Reviver company so far. This manufacturer’s plates, known as Rplate, come in both corded and corded versions, the latter being reserved for commercial fleets only. Reviver claims a battery life of five years as the e-ink only consumes power when the image changes.
The Rplate numbers have caught the attention of experts as they come with a SIM card for remote tracking and updating. For example, one of the features of electronic ink plates is a notification that a vehicle is stolen and moved without the knowledge of its owner. In this case, the number may change to the inscription “Stolen” (“STOLEN”).
It is worth noting that Reviver digital plates began appearing on California roads back in 2017 as part of a pilot program. The company says that since the start of the program and until the official legalization of Rplate, about 10,000 numbers were put into use.
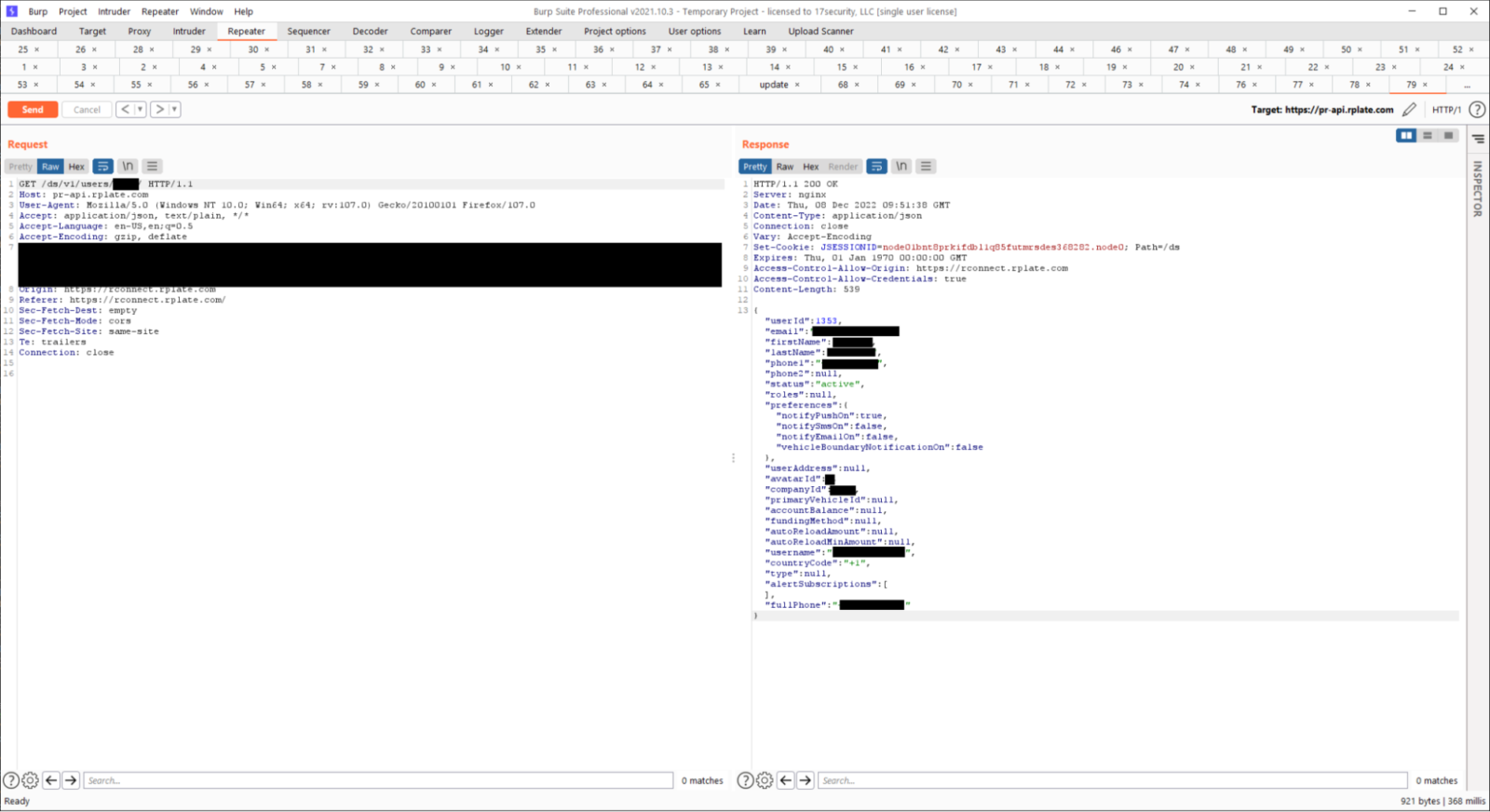
After creating a new Reviver account, the researchers found that this account was given a unique JSON “company” object that allowed them to add sub-users. Several other JSON fields were also editable, including one that specified the account type as CONSUMER .
However, it was not possible to change the value to some other one right away, since other types of accounts could not be found in the mobile application code. Then Curry and his colleagues decided to go the other way and turned to the password reset URL used by Reviver.
As it turned out, the JavaScript on the site contained a complete list of roles, and this allowed the researchers to change their account type to any other. They ended up gaining access to a role called REVIVER, with which the site’s user interface didn’t work properly. The researchers quickly figured out that this was an administrator account, not intended to interact with the user interface at all.
Worse, in addition to privilege escalation, the REVIVER role gave access to any dealership that handled digital numbers, allowing Curry to remotely change the default images from “DEALER” to anything else.