P2P-botnet FritzFrog attacks SSH servers
Guardicore Labs analysts have told about the discovery of the FritzFrog, written in Go malware, which has been attacking SSH servers since the beginning of 2020, and discovery of P2P botnet, active at the same name.
According to the researchers, currently the botnet has carried out about 13,000 attacks and hacked at least 500 SSH servers belonging to government, educational, financial, medical and telecommunications organizations and institutions around the world. The attacks are known to have affected well-known universities in the United States and Europe, as well as a railway company.The main goal of FritzFrog is to mine Monero cryptocurrency. To do this, an XMRig miner is deployed on the infected systems and connected to the web.xmrpool.eu pool via port 5555.
Interestingly, the P2P protocol that uses a botnet is proprietary and is not based on any existing implementation like μTP. According to the researchers, this may indicate that professionals stand behind the creation of FritzFrog. So, analysts note that they were able to identify some similarities between FritzFrog and the Rakos botnet, discovered in 2016.
“With its decentralized infrastructure, FritzFrog distributes control among all of its nodes. There is no single point of failure in this network, and peers constantly communicate with each other to keep the network running, resilient and relevant”, — write the researchers.
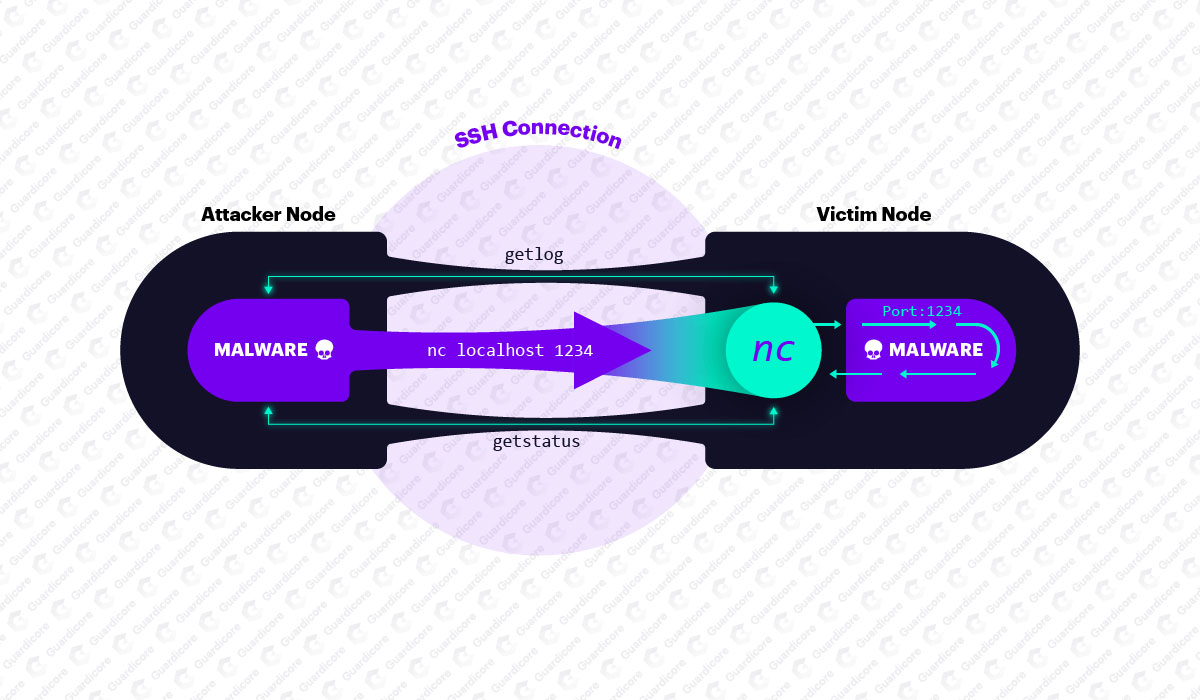
If the brute-force SSH server succeeds, the malware leaves almost no traces on the attacked system, since it runs in memory and is classified as fileless malware. After starting FritzFrog, the malware is unpacked under the names ifconfig and NGINX and listens on port 1234 waiting for commands.
Since such communications are not difficult to detect, attackers connect to the victim via SSH, using netcat. It is also worth mentioning that the payload files are transferred between peers in a BitTorrent style using sharded data transfers.
Typically, the very first command it receives connects the victim machine to the P2P botnet. Other AES-encrypted commands include adding the SSH-RSA public key to the authorized_keys file to create a backdoor, as well as running shell commands to monitor the infected machine’s resources, CPU usage, and network monitoring. If some processes on the server take up CPU resources, malware can kill them so that the miner can work more efficiently.
“Weak passwords are the main driving force behind FritzFrog attacks. We recommend choosing strong passwords and using public key authentication, which is much safer. Routers and IoT devices often have open SSH and are therefore vulnerable to FritzFrog. Consider changing their SSH port or completely disabling SSH access if not in use”, — warn Guardicore Labs experts.
Interestingly, TrendMicro reported that the influence of mining malware declined by almost 70% during 2019, but this year it became known that Blue Mockingbird hackers cracked thousands of corporate systems to mine Monero. And now there’s FritzFrog. 2020, what are you doing with us?





