Earlier this week, as part of June’s “Update Tuesday,” Microsoft fixed the new vulnerability CVE-2020-1206 in its products. A bug that threatened the SMB protocol received the name SMBleed. It allows an attacker remotely and without authentication leak data from kernel memory.
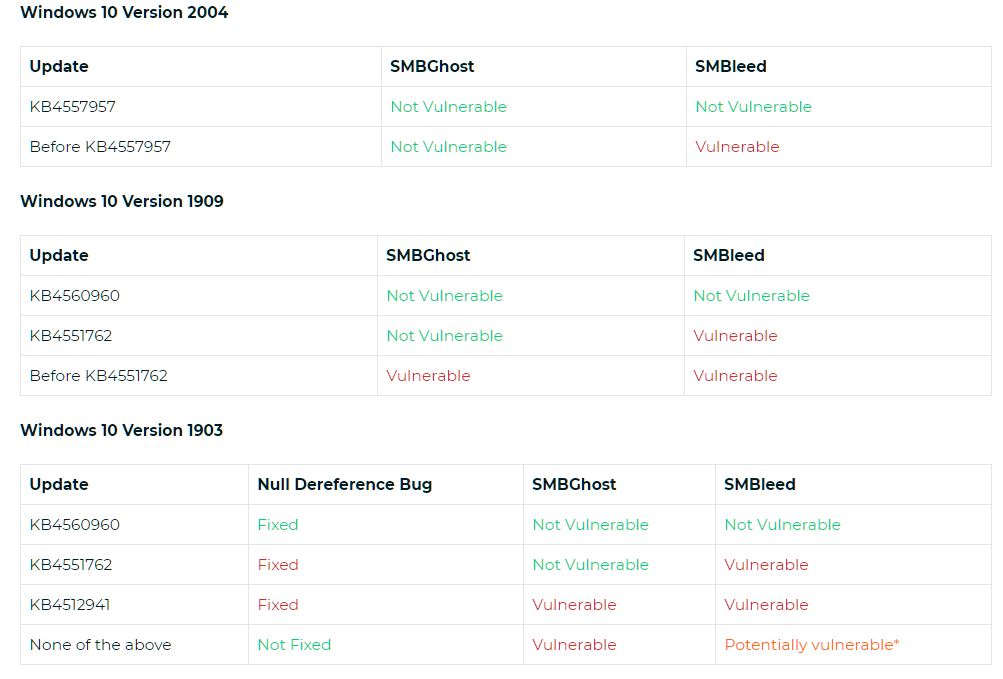
ZecOps specialists discovered the vulnerability, and they say that a fresh problem can be combined with another similar vulnerability – SMBGhost (CVE-2020-0796, also known as CoronaBlue, NexternalBlue and BluesDay), patches for which were already released in March 2020 and for which was first demonstrated and then published an RCE exploit.As with SMBGhost, the root of the SMBleed problem lies in the SMB 3.1.1 compression engine, and the bug affects that way, in which protocol handles certain requests. Windows 10 and Windows Server versions 1903, 1909, and 2004 (but not earlier versions) are vulnerable to the problem.
“To exploit this vulnerability on a server, an unauthenticated attacker could send a specially crafted package to the target SMBv3 server. To exploit this vulnerability for a client, an unauthorized attacker must configure the malicious SMBv3 server and convince the user to connect to it”, — said in the official Microsoft security bulletin.
Although patches for SMBleed are already available, Microsoft offers other methods to solve this problem, for example, disabling SMBv3 compression. Researchers also note that it is possible to protect against SMBleed and SMBGhost by blocking TCP port 445, increasing host isolation and disabling SMB 3.1.1 compression. Although researchers still do not recommend applying these methods.
Experts have already published a PoC exploit for SMBleed, but explain that for the correct work of the exploit user needs credentials, as well as access to writing on the shared resource. However, it is also noted that the bug can be used without authentication. So, the experts themselves combined SMBleed with SMBGhost to achieve RCE (Remote Code Execution).
The exploit for this scenario was also posted in the public domain, and soon experts plan to publish technical details of such an attack. In the meantime, a demonstration of the attack can be seen below.