Black Kingdom ransomware attacks ProxyLogon vulnerabilities
Information security specialist Marcus Hutchins from Kryptos Logic noticed that Black Kingdom ransomware attacks ProxyLogon vulnerabilities on Microsoft Exchange servers.
This malware was first discovered in June last year, when it exploited vulnerabilities in Pulse Secure VPN products to compromise corporate networks and then install a ransomware.Hutchins wrote that the ransomware operators gain access to the Exchange servers and leave a ransom note there, claiming to have encrypted the victim’s files. The hackers are demanding a ransom of $ 10,000 for a key to decrypt data. However, the specialist reported that the Black Kingdom cannot encrypt the victims’ files, essentially leaving the servers untouched.
“Someone just ran this script on all vulnerable Exchange servers via ProxyLogon vulnerability. It claims to be BlackKingdom “Ransomware”, but it doesn’t appear to encrypt files, just drops a ransom not to every directory”, — specialist wrote on his Twitter.
Unfortunately, the hackers quickly realized their mistake. According to experts from Arete IR, Sophos and Speartip, attacks changed at the beginning of this week, and now the malware actually encrypts files. Alas, this is confirmed by the well-known information security expert Kevin Beaumont, a threat analyst at Microsoft.
The number of victims is still unknown, but the own sources of The Record claim that at least one large company in the automotive industry was affected.
Michael Gillespie, creator of ID Ransomware, told reporters that at least 30 companies were affected, and they are located in the United States, Canada, Austria, Switzerland, Russia, France, Israel, Great Britain, Italy, Germany, Greece, Australia and Croatia.
Recall that in early March 2021, Microsoft engineers released unscheduled patches for four vulnerabilities in the Exchange mail server, which the researchers gave the general name ProxyLogon (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065).
These vulnerabilities can be chained together and exploited to allow an attacker to authenticate on the Exchange server, gain administrator rights, install malware, and steal data.
More than ten hack groups are engaged in attacks on vulnerable servers, deploying web shells, miners and ransomware on the servers.
Let me also remind you that WSJ Says Microsoft Partners May Be Involved in Cyberattack on Exchange Servers.
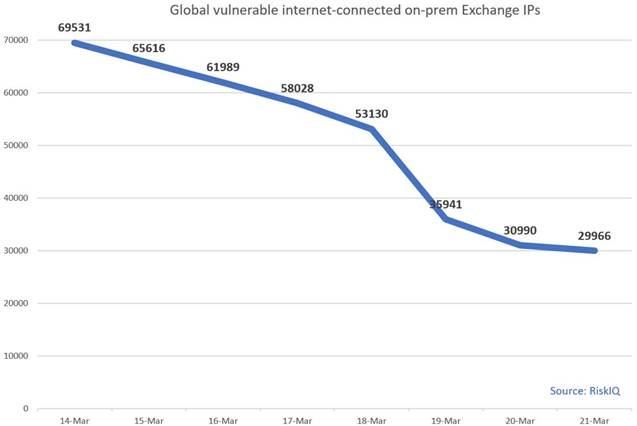
Meanwhile, Microsoft experts report that the fight against ProxyLogon is in full swing. Microsoft said last weekend that roughly 92% of all Exchange servers have received patches and are now protected from malicious attacks. So, according to the OS manufacturer, out of 400,000 Exchange servers deployed worldwide, only 30,000 are still vulnerable to attacks.
Thus, now the number of problem servers has decreased by 56% compared to the 69,500 servers, which Microsoft called a week earlier.