Indian security specialist Bhavuk Jain received $100,000 from Apple via bug bounty program for detecting a critical vulnerability in Sign in with Apple.
The problem allowed remote attackers to bypass authentication and seize user accounts in third-party services and applications that supported Sign in with Apple.Recall that the Sign in with Apple functionality was introduced last year at WWDC 2019. This mechanism allows users to log in to third-party applications and services using Apple ID and iCloud (this is not only about iOS applications).
Essentially, Sign in with Apple works the same way as similar systems provided by Facebook and Google, however, Apple developers put more emphasis on user privacy, the fight against snooping and spam.
“So, the Sign in with Apple button can be integrated into any application, and most often, the user only needs to authenticate with FaceID or Touch ID on his device without revealing any personal data and location”, – recalls Bhavuk Jain on his blog.
The researcher says that the problem he discovered is related to how client validation is implemented on the client side, even before initiating the request from the Apple authentication server.
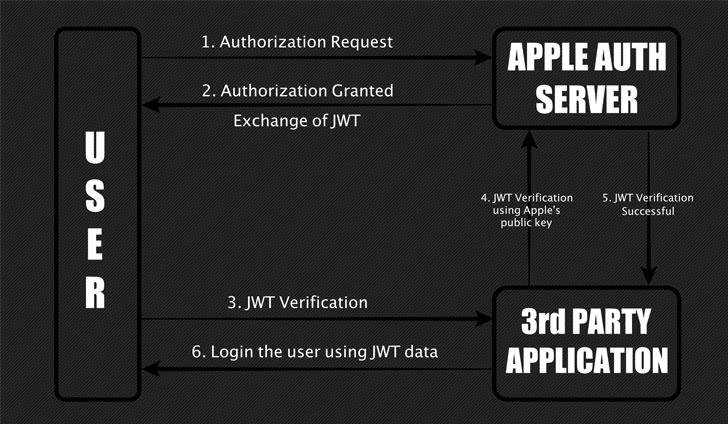
So, during user authentication through Sign in with Apple, the server generates a JSON Web Token (JWT) containing secret information that a third-party application uses to verify the identity of the user that is logged in. However, the specialist found that although Apple asks users to log in to the account before the initial request, the system does not validate without confirming that the next person requests the JSON web token.
The lack of validation allowed attackers to trick Apple’s servers by providing them with an Apple ID belonging to the victim and forcing them to generate a JWT that would allow, using the victim’s identity, to log into the account of a third-party application or service.
“I found that I can request a JWT for any email-ID, and when the signature of these tokens was verified using the Apple public key, it turned out that they are valid. This means that an attacker can fake a JWT by associating any email identifier with it and gaining access to the victim’s accounts”, — the researcher writes.
Jain notes that the vulnerability works even if the user decided to hide his email identifier from third-party services, and can be used to register a new account with the victim’s Apple ID.

“The consequences of [exploiting] this vulnerability would be critical, because the problem allowed a complete capture of the record. Many developers have integrated Sign in with Apple into their products, as this is a prerequisite for applications that support login via social networks. For example, Sign in with Apple use Dropbox, Spotify, Airbnb, Giphy”.
Currently, Apple developers have already fixed the problem and report that hackers did not use the bug to compromise other people’s accounts. However, recently about the 0-day vulnerability discovered by ZecOps specialists, the apple claimed the same thing, however, it looks like they were mistaken.
Recall that only in March Apple fixed 27 code execution vulnerabilities in a number of products.