306 vulnerabilities were found in popular Android applications, and only 18 of them received patches
Researchers from Columbia University created CRYLOGGER, a tool designed to dynamically analyze Android applications and detect unsafe cryptographic practices, and found 306 vulnerabilities in Android applications.
They are convinced that they have developed a powerful tool that can be used alongside with CryptoGuard. The idea is that the tools will complement each other, as CryptoGuard is a static analyzer (analyzes the source code before execution), and CRYLOGGER is a dynamic analysis tool (analyzes the code at runtime).Using CRYLOGGER, scientists tested 1,780 apps from 33 different categories on the Google Play Store, selecting the most popular for September and October 2019. The tool tested applications on 26 points, each of which represents one rule for using cryptography.
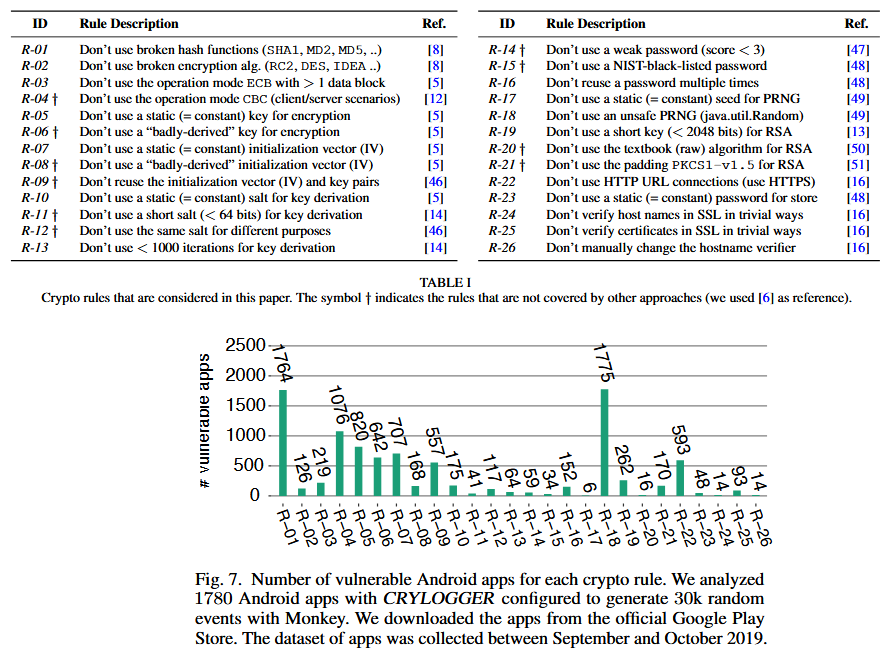
As a result, the team of specialists managed to identify serious errors in 306 applications, and the most common bugs were:
- rule #18 (1775 applications): do not use an unsafe pseudo-random number generator;
- rule #1 (1764 applications): do not use unreliable hash functions (SHA1, MD2, MD5, and so on)
- rule #4 (1076 Applications): Don’t use CBC mode (in client/server scenarios).
The researchers say that after finding bugs, they contacted the developers of all 306 problematic applications, though, unfortunately, this did not help much.
“All of these apps are popular, with hundreds of thousands to 100,000,000 downloads. Unfortunately, only 18 developers responded to our e-mail, and only 8 of them responded to us repeatedly, providing good feedback on our research”, — write the scientists.
It is also worth noting that some errors were found not in the code of the applications themselves, but in the code of the Java libraries that used the developers. The researchers tried to contact the authors of six popular libraries, but in this case, they also did not succeed and received answers from only two of them.
Since most developers never released patches for their applications and libraries, the researchers decided not to publish the names of the vulnerable products due to ear of possible exploitation and abuse.
Let me remind you about recent information that patches for Android soon will reach users faster.
By the way, do you want to look at simple picture that turns a smartphone with Android into a piece of stone?





