Police Shut Down One of the Largest Darknet Marketplaces, Genesis
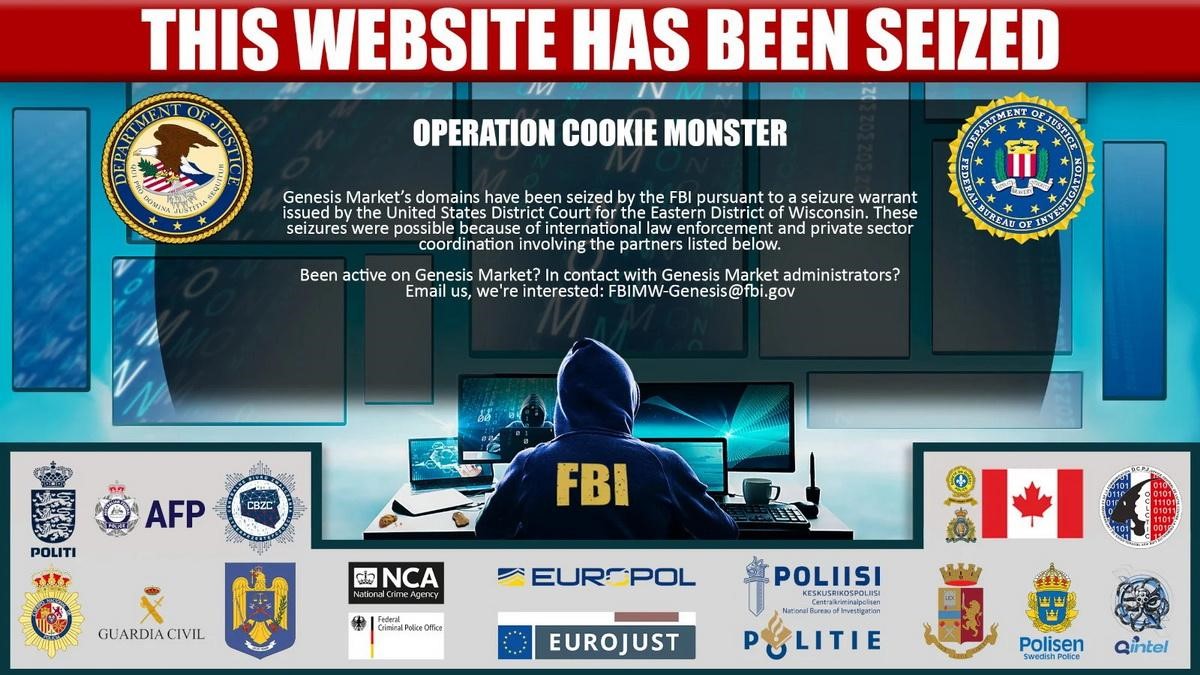
One of the largest marketplaces on the dark web, Genesis, was shut down as part of the FBI-coordinated international Cookie Monster operation. Genesis sold stolen credentials, cookies, and even pre-made virtual identities.
The site has been linked to a variety of financially motivated attacks around the world, ranging from simple scams to ransomware attacks.Although law enforcement officers have not yet made official statements, when trying to enter the Genesis website, it displays a special “stub” informing about the liquidation of the FBI resource.
The Record edition, citing its own sources, reports that in connection with the closure of the resource and the confiscation of its servers, many arrests are currently being made around the world.
And also let me remind you that we wrote that The Government of Germany Closed Hacker Hosting FlyHosting, and also that Law Enforcement Officers Closed the Underground WT1SHOP Marketplace That Sold Bank Cards and Credentials.
The media also reported that BreachForums Closed Due to Fears That Law Enforcement Officers Gained Access to the Servers.
At the same time, judging by the banner of law enforcement officers, the administrators of the trading platform have not yet been identified or arrested, as the FBI is asking everyone who has any information about them to get in touch.
Recorded Future analysts remind that Genesis was launched at the end of 2017 and by 2020 has become one of the most popular marketplaces, standing out from the Russian Market and 2easy Shop. Genesis mainly sold credentials (including for Gmail, Netflix, Spotify, WordPress, PayPal, Reddit, Amazon, LinkedIn, Cloudflare, Twitter, Zoom, Ebay and so on) cookies and so-called fingerprints (digital fingerprints, bots , and to put it simply – ready-made virtual personalities) for various devices.
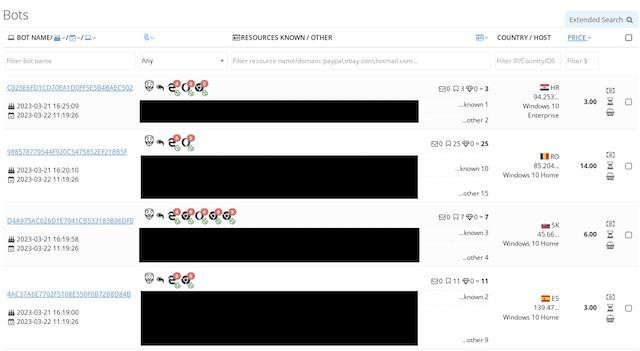
Selling bots on Genesis
Access to Genesis could only be obtained by invitation, but such an invite was not difficult to find in a regular search engine. The researchers say the invitations were widely available and were often distributed even through YouTube. In addition, Genesis even had its own Wiki explaining to beginners how everything works.
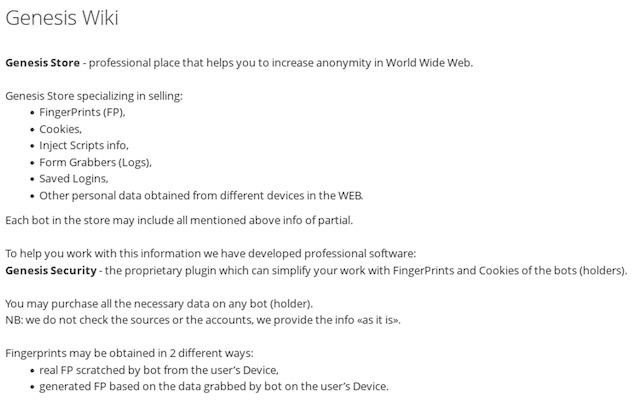
As mentioned above, unlike competitors, Genesis provided criminals with access to digital fingerprints that allowed hackers to impersonate victims, assigning their IP addresses, session cookies, OS information, installed plugins, and so on. Thus, criminals could access subscription platforms (eg Netflix, Amazon) as well as online banking services without arousing the suspicions of security systems, or bypass multi-factor authentication.
Usually such prints were sold along with a list of services to which the victim has access (Netflix, Amazon, eBay accounts, and so on). In addition, the bots could provide access to other accounts not automatically listed, such as corporate networks. Once purchased, the bot could be imported into the criminal-developed Genesis Security browser, which was even available as an extension for other browsers. Depending on the type of account, buyers could pay less than $10 to access the digital “mask”.
The data for these bots was mainly collected using infostealers, and Genesis, unlike its competitors, did not have such a wide list of permanent “suppliers” like RedLine, Vidar, Raccoon or META.
According to KELA experts who studied the activity of the marketplace back in 2020, most of the stolen data on Genesis came from the AZORult malware.
Genesis has sold over 135,000,000 digital prints since 2018, according to Recorded Future.





