About 5.5% of detected vulnerabilities used for implementation real attacks
A group of researchers from the Virginia University in cooperation with Cyentia and RAND companies, published the results of risk analysis for application various strategies to fix vulnerabilities.
After examining 476 thousand vulnerabilities found from 2009 to 2018, it was revealed that only 4,183 of them (5.5%) were used to carry out real attacks.“The ability to effectively assess the risk of a vulnerability, to understand how prevalent it is, and to makeinferences about the risk it poses to either a single firm, or to sectors of critical infrastructure, is anextraordinarily important matter. Indeed, it is one of the foundations of information security riskmanagement, domestic protection of critical infrastructure, and even national security”, — consider researchers.
The resulting figure is five times higher than previously published forecasts, in which the number of exploited problems was estimated at about 1%.
At the same time, no correlation was found between the publication in open access exploits’ prototypes and attempts to exploit vulnerabilities. From all the facts of exploitation of vulnerabilities that are known to researchers, only in half of the cases exploit was published in open sources. Absence of exploit’s prototype does not stop the attackers, who, if necessary, create exploits on their own.
Among other conclusions, one can note the demand for exploitation of mainly vulnerabilities with a high level of danger according to CVSS classification. In almost half of the attacks, were used vulnerabilities with a score of at least 9.
The total number of exploit prototypes published during the period estimated at 9726. The exploit data used in the study was obtained from the collections of Exploit DB, Metasploit, D2 Security’s Elliot Kit, Canvas Exploitation Framework, Contagio, Reversing Labs and Secureworks CTU.
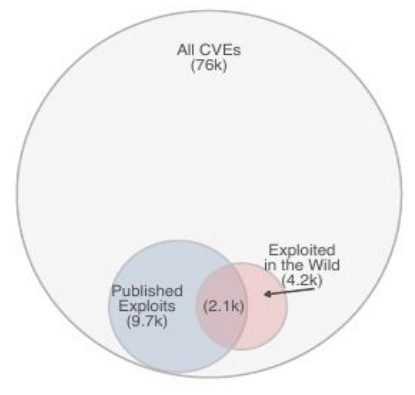
The study was conducted to determine the optimal balance between use of updates in identifying any vulnerabilities and eliminating only the most dangerous problems.
In the first case, the high efficiency of protection is provided, but large resources are required to maintain the infrastructure, which is spent mainly on fixing minor problems.
In the second case, there is a high risk of missing a vulnerability that can be used to attack. The study showed that when deciding to install an update with the elimination of a vulnerability, you should not rely on the lack of a published prototype of the exploit and the chance of exploitation directly depends on the level of danger of the vulnerability.
Source: https://weis2019.econinfosec.org






One Comment